MicroK8s : ダッシュボードを有効にする2020/08/03 |
|
MicroK8s クラスターでダッシュボードを有効にする場合は以下のように設定します。
|
| [1] | プライマリーノードで、ダッシュボード アドオンを有効にします。 |
|
root@dlp:~# microk8s enable dashboard dns Enabling Kubernetes Dashboard Enabling Metrics-Server clusterrole.rbac.authorization.k8s.io/system:aggregated-metrics-reader created clusterrolebinding.rbac.authorization.k8s.io/metrics-server:system:auth-delegator created rolebinding.rbac.authorization.k8s.io/metrics-server-auth-reader created apiservice.apiregistration.k8s.io/v1beta1.metrics.k8s.io created serviceaccount/metrics-server created deployment.apps/metrics-server created service/metrics-server created clusterrole.rbac.authorization.k8s.io/system:metrics-server created clusterrolebinding.rbac.authorization.k8s.io/system:metrics-server created clusterrolebinding.rbac.authorization.k8s.io/microk8s-admin created Adding argument --authentication-token-webhook to nodes. Applying to node node01.srv.world. Metrics-Server is enabled Applying manifest serviceaccount/kubernetes-dashboard created service/kubernetes-dashboard created secret/kubernetes-dashboard-certs created secret/kubernetes-dashboard-csrf created secret/kubernetes-dashboard-key-holder created configmap/kubernetes-dashboard-settings created role.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created deployment.apps/kubernetes-dashboard created service/dashboard-metrics-scraper created deployment.apps/dashboard-metrics-scraper created If RBAC is not enabled access the dashboard using the default token retrieved with: token=$(microk8s kubectl -n kube-system get secret | grep default-token | cut -d " " -f1) microk8s kubectl -n kube-system describe secret $token In an RBAC enabled setup (microk8s enable RBAC) you need to create a user with restricted permissions as shown in: https://github.com/kubernetes/dashboard/blob/master/docs/user/access-control/creating-sample-user.md Enabling DNS Applying manifest serviceaccount/coredns created configmap/coredns created deployment.apps/coredns created service/kube-dns created clusterrole.rbac.authorization.k8s.io/coredns created clusterrolebinding.rbac.authorization.k8s.io/coredns created Restarting kubelet Adding argument --cluster-domain to nodes. Applying to node node01.srv.world. Adding argument --cluster-dns to nodes. Applying to node node01.srv.world. Restarting nodes. Applying to node node01.srv.world. DNS is enabledroot@dlp:~# microk8s kubectl get services -n kube-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE dashboard-metrics-scraper ClusterIP 10.152.183.56 <none> 8000/TCP 119s kube-dns ClusterIP 10.152.183.10 <none> 53/UDP,53/TCP,9153/TCP 119s kubernetes-dashboard ClusterIP 10.152.183.7 <none> 443/TCP 119s metrics-server ClusterIP 10.152.183.50 <none> 443/TCP 2m # セキュリティトークン確認 # [token:] 行の二列目が該当 root@dlp:~# microk8s kubectl -n kube-system describe secret $(microk8s kubectl -n kube-system get secret | grep default-token | awk '{print $1}')
Name: default-token-n9m8r
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: default
kubernetes.io/service-account.uid: 823d56bf-ba7a-46c2-915b-37e9bbdf3331
Type: kubernetes.io/service-account-token
Data
====
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6ImRlWTdDUnpYaVd5N2hxVkczblpqNldyMzFzNWptQ3FjeW.....
# 外部からもアクセスできるようにポートフォワードする root@dlp:~# microk8s kubectl port-forward -n kube-system service/kubernetes-dashboard --address 0.0.0.0 10443:443 Forwarding from 0.0.0.0:10443 -> 8443 |
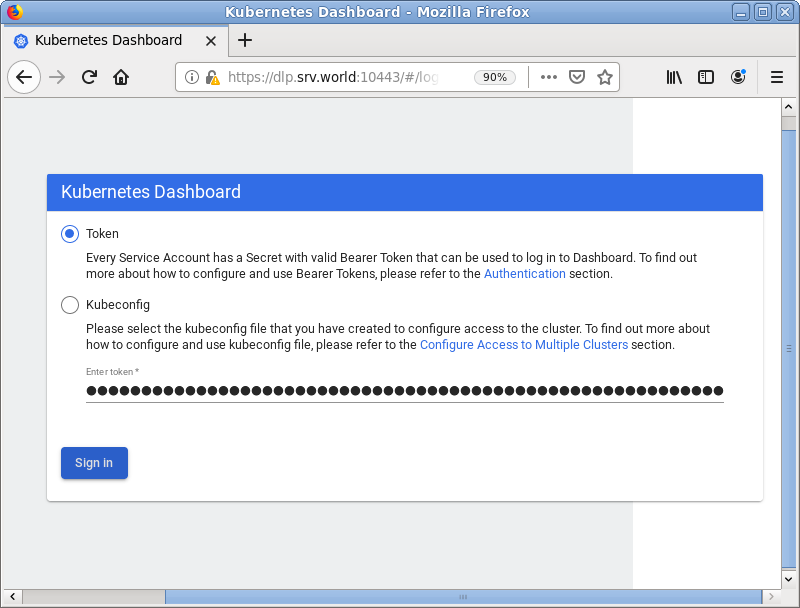
| [2] | ローカルネットワーク内の任意のクライアントコンピューターで Web ブラウザーを起動し、[https://(MicroK8s プライマリーノードのホスト名 または IP アドレス):10443/] にアクセスします。以下のような画面が表示されたら、[1] で確認したセキュリティトークンを コピー & ペーストして [Sing In] ボタンをクリックします。なお、下例の画面は英語表示となっていますが、日本語 OS でアクセスすれば日本語で表示されます。 |
|
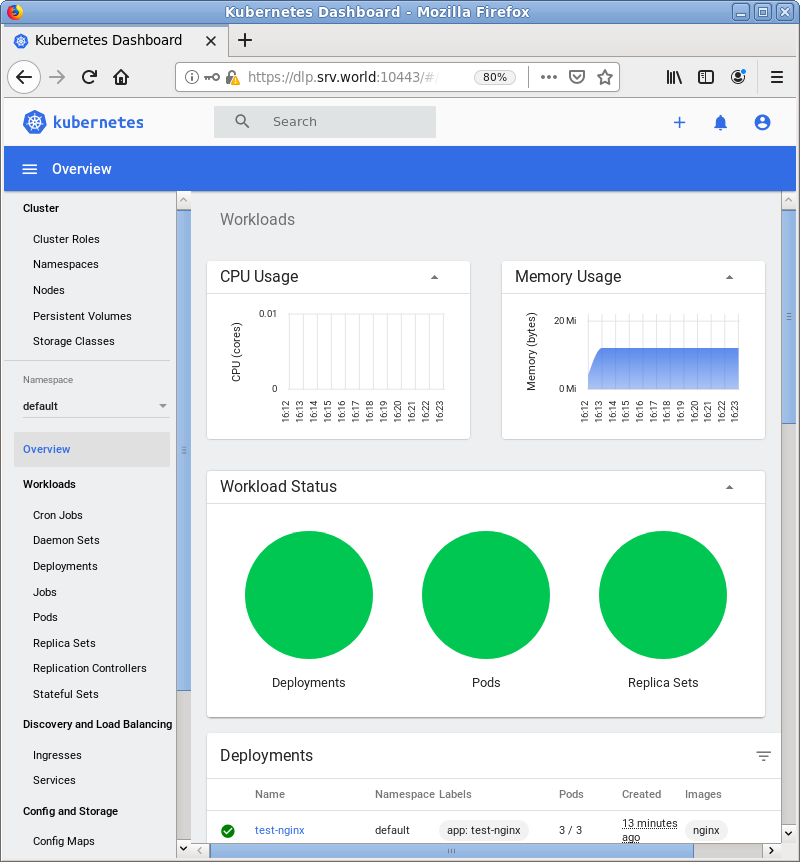
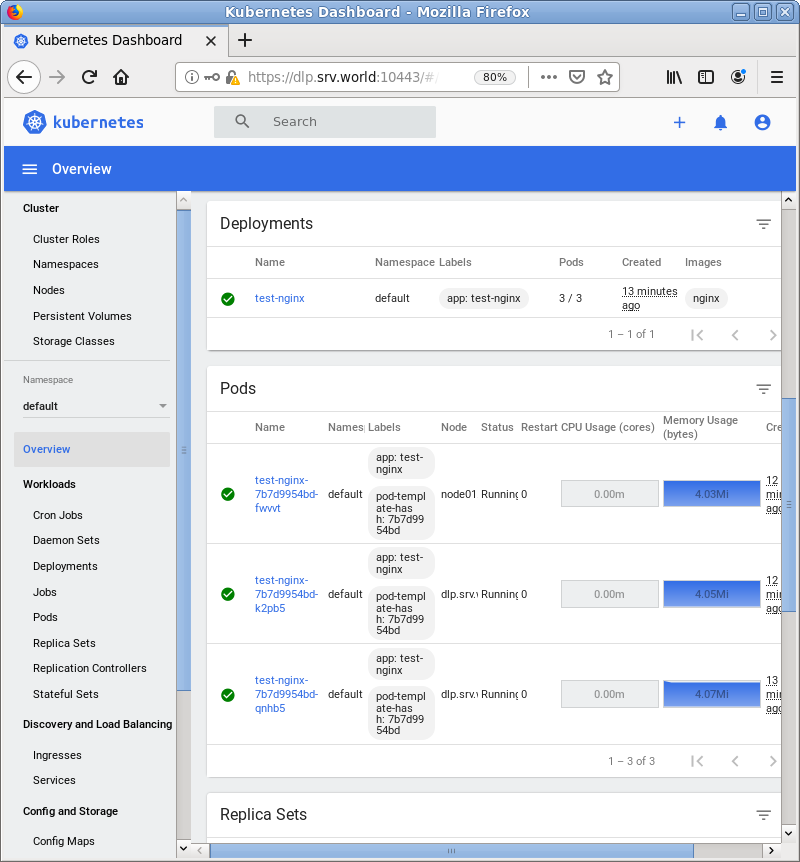
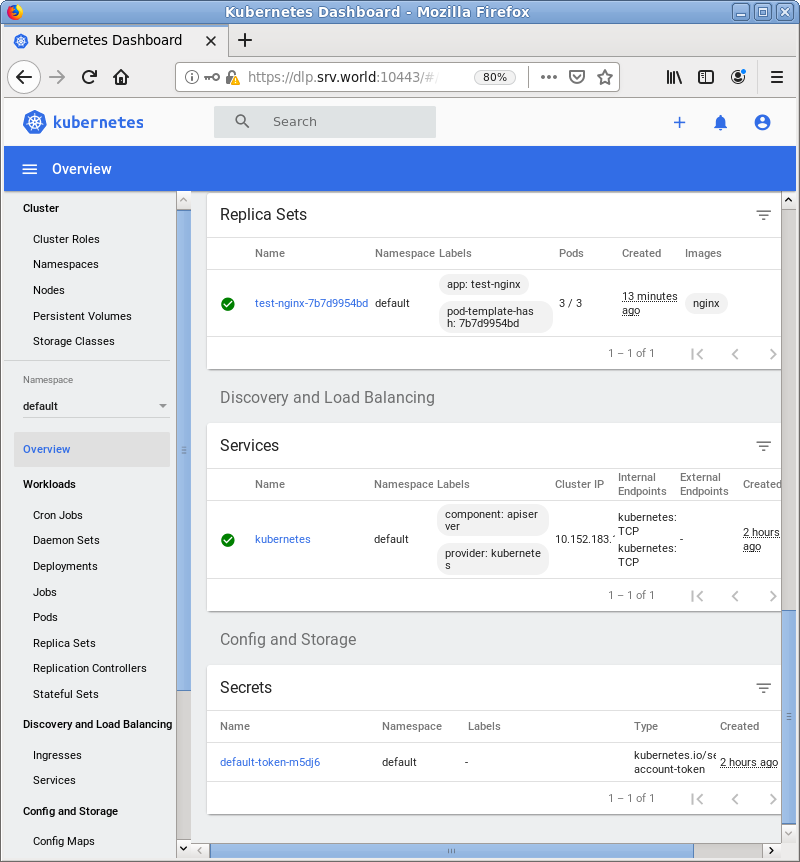
| [3] | 認証が成功すると MicroK8s クラスターのダッシュボードが表示されます。 |
|
|
|
関連コンテンツ