SSL 設定2008/08/16 |
| SSLでの暗号化通信ができるように設定します。証明書は独自に作成して使用することにします。 しかし独自に作成した証明書ではアクセス時に警告が出るため、商用で使う場合は ベリサイン 等の正規の認証局が発行する証明書を利用した方がよいでしょう。 |
|
# vi /etc/sfw/openssl/openssl.cnf # 43行目:変更 dir = /etc/sfw/openssl/demoCA # 47行目:コメント解除 unique_subject = no # cd /etc/sfw/openssl # perl /usr/sfw/bin/CA.pl -newca CA certificate filename (or enter to create) Making CA certificate ... Generating a 1024 bit RSA private key .......++++++ ...........++++++ writing new private key to './demoCA/private/cakey.pem' Enter PEM pass phrase: # パスフレーズ Verifying - Enter PEM pass phrase: ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [US]: JP State or Province Name (full name) [Some-State]: Hiroshima Locality Name (eg, city) [Newbury]: Hiroshima Organization Name (eg, company) [My Company Ltd]: Server Linux Organizational Unit Name (eg, section) []: IT Solution Common Name (eg, YOUR name) []: www.srv.world Email Address []: root@srv.world # mkdir /etc/apache2/certs # openssl req -new -keyout /etc/apache2/certs/server.key -out csr.pem Generating a 1024 bit RSA private key ...........++++++ ....................++++++ writing new private key to '/etc/apache2/certs/server.key' Enter PEM pass phrase: # パスフレーズ入力 Verifying - Enter PEM pass phrase: ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [US]: JP State or Province Name (full name) [Some-State]: Hiroshima Locality Name (eg, city) [Newbury]: Hiroshima Organization Name (eg, company) [My Company Ltd]: Server Linux Organizational Unit Name (eg, section) []: IT Solution Common Name (eg, YOUR name) []: www.srv.world Email Address []: root@srv.world Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: # 空Enter An optional company name []: # 空Enter # openssl rsa -in /etc/apache2/certs/server.key -out /etc/apache2/certs/server.key Enter pass phrase for /etc/apache2/certs/server.key: # パスフレーズ入力 writing RSA key # openssl ca -out server.crt -infiles csr.pem Using configuration from /etc/sfw/openssl/openssl.cnf Enter pass phrase for /etc/sfw/openssl/demoCA/private/cakey.pem: # パスフレーズ入力 Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Oct 9 11:42:19 2007 GMT Not After : Oct 8 11:42:19 2008 GMT Subject: countryName = JP stateOrProvinceName = Hiroshima organizationName = Server Linux organizationalUnitName = IT Solution commonName = ns.srv.world emailAddress = root@srv.world X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX X509v3 Authority Key Identifier: keyid:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX DirName:/C=JP/ST=Hiroshima/L=Hiroshima/O=Server World/OU=IT Solution/CN=ns.srv.world/emailAddress=root@srv.world serial:00 Certificate is to be certified until Oct 8 11:42:19 2008 GMT (365 days) Sign the certificate? [y/n]: y 1 out of 1 certificate requests certified, commit? [y/n] y Write out database with 1 new entries Data Base Updated # cp server.crt /etc/apache2/certs/server.crt # vi /etc/apache2/ssl.conf # 87行目:サーバー名指定 ServerName www.srv.world:443 # 88行目:管理者アドレス指定 ServerAdmin root@srv.world # 112行目:変更 SSLCertificateFile /etc/apache2/certs/server.crt # 120行目:変更 SSLCertificateKeyFile /etc/apache2/certs/server.key # svccfg svc:> select apache2 svc:/network/http:apache2> editprop # 7行目:コメント解除し変更 setprop httpd/ssl = boolean: ( true )svc:/network/http:apache2> quit # svcadm refresh apache2 # svcadm restart apache2
|
| 前節(1)で作ったテストページに https でアクセスしてみます。独自証明書なので以下のような警告が出ます。 | |
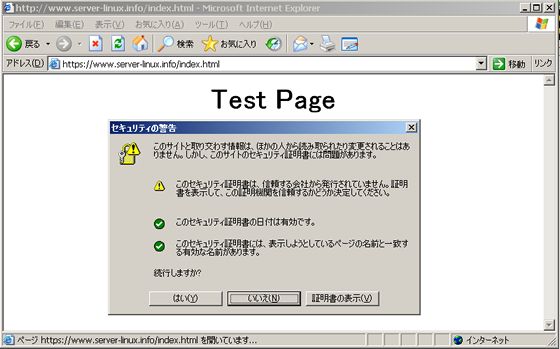
|
| 「はい」をクリックすると以下のように正常にアクセスすることができます。 しかし独自証明書は以上のような警告が出るため(暗号化通信には全く問題ないのですが)、 利用機会というと、知り合い同士での暗号化通信が必要なときくらいで、 不特定多数の人には信頼性が薄くなるため、 あまり実用性はないかもしれません。 | |
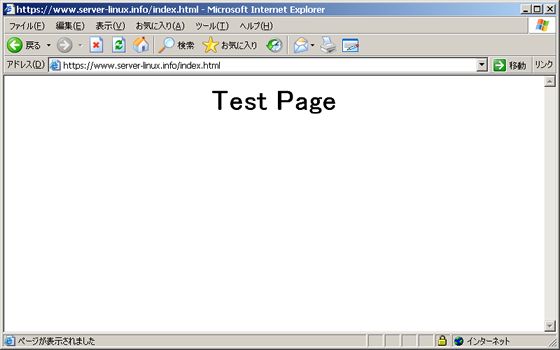
|
関連コンテンツ