FreeIPA : FreeIPA trust AD2022/03/23 |
|
FreeIPA ドメインと Windows Active Directory ドメイン間で信頼関係を構築する クロス フォレスト トラスト の設定です。
Windows Active Directory ドメインのユーザーアカウントで FreeIPA ドメインのリソースにアクセスできるようになります。 当例では以下のような環境を例にします。
+----------------------+ | +----------------------+ | [ FreeIPA (CentOS) ] |10.0.0.40 | 10.0.0.100| [ AD (Win 2022) ] | | dlp.ipa.srv.world +----------+-----------+ fd3s.ad.srv.world | | | | | +----------------------+ +----------------------+ |
| [1] | 構築済みの FreeIPA サーバー上で FreeIPA trust AD をインストールします。 |
|
[root@dlp ~]#
[root@dlp ~]# dnf -y install ipa-server-trust-ad ipa-adtrust-install The log file for this installation can be found in /var/log/ipaserver-adtrust-install.log ============================================================================== This program will setup components needed to establish trust to AD domains for the IPA Server. This includes: * Configure Samba * Add trust related objects to IPA LDAP server To accept the default shown in brackets, press the Enter key. Configuring cross-realm trusts for IPA server requires password for user 'admin'. This user is a regular system account used for IPA server administration. # FreeIPA admin パスワードで応答 admin password: WARNING: The smb.conf already exists. Running ipa-adtrust-install will break your existing samba configuration. # smb.conf を上書きしてよいかの確認 Do you wish to continue? [no]: yes Do you want to enable support for trusted domains in Schema Compatibility plugin? This will allow clients older than SSSD 1.9 and non-Linux clients to work with trusted users. # slapi-nis を有効にするか否か # SSSD 1.9 以前の古い Linux OS などとの互換性 Enable trusted domains support in slapi-nis? [no]: The following operations may take some minutes to complete. Please wait until the prompt is returned. Configuring CIFS [1/23]: validate server hostname [2/23]: stopping smbd [3/23]: creating samba domain object ..... ..... ============================================================================= Setup complete You must make sure these network ports are open: TCP Ports: * 135: epmap * 138: netbios-dgm * 139: netbios-ssn * 445: microsoft-ds * 1024..1300: epmap listener range * 3268: msft-gc UDP Ports: * 138: netbios-dgm * 139: netbios-ssn * 389: (C)LDAP * 445: microsoft-ds See the ipa-adtrust-install(1) man page for more details ============================================================================= # firewalld 稼働中の場合は以下も設定 [root@dlp ~]# firewall-cmd --add-service=freeipa-trust success [root@dlp ~]# firewall-cmd --runtime-to-permanent success |
| [2] | FreeIPA サーバー上で DNS 関連の設定を追加します。 |
|
# ipa dnsforwardzone-add [AD のドメイン名] --forwarder=[AD の IP アドレス] --forward-policy=only [root@dlp ~]# ipa dnsforwardzone-add ad.srv.world --forwarder=10.0.0.100 --forward-policy=only Server will check DNS forwarder(s). This may take some time, please wait ... Zone name: ad.srv.world. Active zone: TRUE Zone forwarders: 10.0.0.100 Forward policy: only # ipa dnszone-mod [IPA のドメイン名] --allow-transfer=[AD の IP アドレス] [root@dlp ~]# ipa dnszone-mod ipa.srv.world --allow-transfer=10.0.0.100 Zone name: ipa.srv.world. Active zone: TRUE Authoritative nameserver: dlp.ipa.srv.world. Administrator e-mail address: hostmaster.ipa.srv.world. SOA serial: 1648005848 SOA refresh: 3600 SOA retry: 900 SOA expire: 1209600 SOA minimum: 3600 BIND update policy: grant IPA.SRV.WORLD krb5-self * A; grant IPA.SRV.WORLD krb5-self * AAAA; grant IPA.SRV.WORLD krb5-self * SSHFP; Dynamic update: TRUE Allow query: any; Allow transfer: 10.0.0.100; |
| [3] | Windows Active Directory 側でも FreeIPA ドメインをゾーンに追加します。 ⇒ dnscmd 127.0.0.1 /ZoneAdd [FreeIPA のドメイン名] /Secondary [FreeIPA の IP アドレス] |
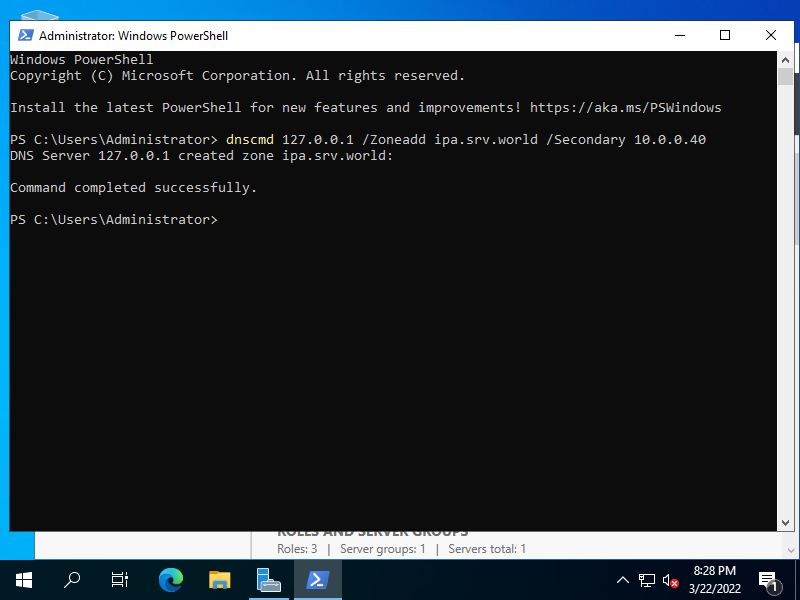
|
| [4] | 名前解決の確認をした後、問題なければ FreeIPA trust AD をセットアップします。 |
|
[root@dlp ~]# dig SRV _ldap._tcp.ipa.srv.world ; <<>> DiG 9.16.23-RH <<>> SRV _ldap._tcp.ipa.srv.world ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 913 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 3 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ; COOKIE: 054a55dba44a8b5601000000623a9457340f92b86268b581 (good) ;; QUESTION SECTION: ;_ldap._tcp.ipa.srv.world. IN SRV ;; ANSWER SECTION: _ldap._tcp.ipa.srv.world. 86400 IN SRV 0 100 389 dlp.ipa.srv.world. _ldap._tcp.ipa.srv.world. 86400 IN SRV 0 100 389 node01.ipa.srv.world. ;; ADDITIONAL SECTION: dlp.ipa.srv.world. 1200 IN A 10.0.0.40 node01.ipa.srv.world. 1200 IN A 10.0.0.61 ;; Query time: 0 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Wed Mar 23 12:30:31 JST 2022 ;; MSG SIZE rcvd: 190[root@dlp ~]# dig SRV _ldap._tcp.ad.srv.world ; <<>> DiG 9.16.23-RH <<>> SRV _ldap._tcp.ad.srv.world ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 9864 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ; COOKIE: 7ac8a9d0c54230ee01000000623a94846202d8eb1778ec4d (good) ;; QUESTION SECTION: ;_ldap._tcp.ad.srv.world. IN SRV ;; ANSWER SECTION: _ldap._tcp.ad.srv.world. 600 IN SRV 0 100 389 fd3s.ad.srv.world. ;; Query time: 798 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Wed Mar 23 12:31:16 JST 2022 ;; MSG SIZE rcvd: 117 # ipa trust-add --type=ad [AD のドメイン名] --admin Administrator --password [root@dlp ~]# ipa trust-add --two-way=true --type=ad ad.srv.world --admin Administrator --password Active Directory domain administrator's password: ----------------------------------------------------- Added Active Directory trust for realm "ad.srv.world" ----------------------------------------------------- Realm name: ad.srv.world Domain NetBIOS name: FD3S01 Domain Security Identifier: S-1-5-21-726412840-3773945212-2352305327 Trust direction: Two-way trust Trust type: Active Directory domain Trust status: Established and verified # 任意の AD ユーザーの情報が取得できるか確認 [root@dlp ~]# id Serverworld@ad.srv.world uid=1596401103(serverworld@ad.srv.world) gid=1596401103(serverworld@ad.srv.world) groups=1596401103(serverworld@ad.srv.world),1596400513(domain users@ad.srv.world) # 必要があれば有効に設定 (初回ログイン時にホームディレクトリを自動生成) [root@dlp ~]# authselect enable-feature with-mkhomedir [root@dlp ~]# systemctl enable --now oddjobd
# 任意の AD ユーザーでログイン可能か確認 [root@dlp ~]# exit logout CentOS Stream 9 Kernel 5.14.0-71.el9.x86_64 on an x86_64 Activate the web console with: systemctl enable --now cockpit.socket dlp login: Serverworld@ad.srv.world Password: [serverworld@ad.srv.world@dlp ~]$ id uid=1596401103(serverworld@ad.srv.world) gid=1596401103(serverworld@ad.srv.world) groups=1596401103(serverworld@ad.srv.world),1596400513(domain users@ad.srv.world) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 # ログインできた |
関連コンテンツ