Apache2 : Configure mod_security2022/05/12 |
|
Enable [mod_security] module to configure Web Application Firewall (WAF).
|
|
| [1] | Install [mod_security]. |
|
root@www:~# apt -y install libapache2-mod-security2
|
| [2] | Enable [mod_security]. |
|
root@www:~# cp -p /etc/modsecurity/modsecurity.conf-recommended /etc/modsecurity/modsecurity.conf
root@www:~#
vi /etc/modsecurity/modsecurity.conf
line 7 : [SecRuleEngine DetectionOnly] is set as default, it does not block actions
# if you'd like to block actions, change to [SecRuleEngine On]
SecRuleEngine DetectionOnly
.....
.....
|
| [3] |
It's possible to write a rule like follows.
⇒ SecRule VARIABLES OPERATOR [ACTIONS]
Each parameter has many kind of values, refer to official documents below.
https://github.com/SpiderLabs/ModSecurity/wiki |
| [4] | For Example, set some rules and verify it works normally. |
|
root@www:~#
vi /etc/modsecurity/localrules.conf # default action when matching rules SecDefaultAction "phase:2,deny,log,status:406" # [etc/passwd] is included in request URI SecRule REQUEST_URI "etc/passwd" "id:'500001'" # [../] is included in request URI SecRule REQUEST_URI "\.\./" "id:'500002'" # [<SCRIPT] is included in arguments SecRule ARGS "<[Ss][Cc][Rr][Ii][Pp][Tt]" "id:'500003'" # [SELECT FROM] is included in arguments SecRule ARGS "[Ss][Ee][Ll][Ee][Cc][Tt][[:space:]]+[Ff][Rr][Oo][Mm]" "id:'500004'" systemctl restart apache2
|
| [5] | Access to the URI which includes words you set and verify it works normally. |
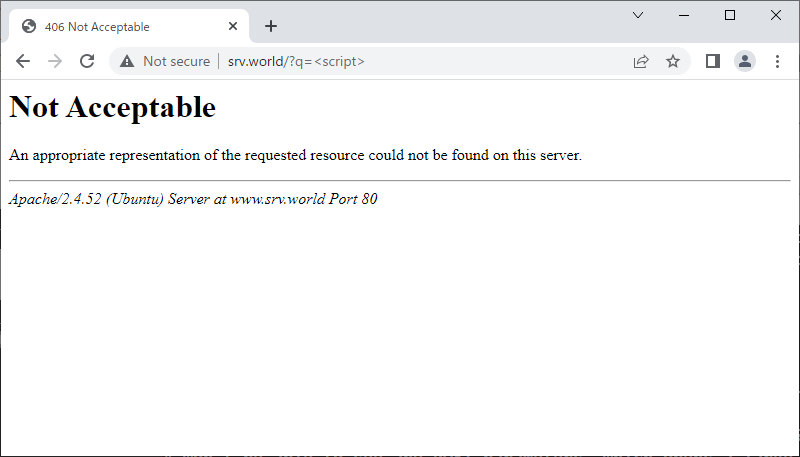
|
| [6] | The logs for [mod_security] is placed in the directory like follows. |
|
root@www:~# cat /var/log/apache2/modsec_audit.log --622ba619-H-- Message: Access denied with code 406 (phase 2). Pattern match "<[Ss][Cc][Rr][Ii][Pp][Tt]" at ARGS:q. [file "/etc/modsecurity/localrules.conf"] [line "7"] [id "500003"] Apache-Error: [file "apache2_util.c"] [line 271] [level 3] [client 10.0.0.5] ModSecurity: Access denied with code 406 (phase 2). Pattern match "<[Ss][Cc][Rr][Ii][Pp][Tt]" at ARGS:q. [file "/etc/modsecurity/localrules.conf"] [line "7"] [id "500003"] [hostname "www.srv.world"] [uri "/"] [unique_id "YnyTEiy-Up3h1XkleOirgAAAAAA"] Action: Intercepted (phase 2) Stopwatch: 1652331282078532 1929 (- - -) Stopwatch2: 1652331282078532 1929; combined=928, p1=759, p2=34, p3=0, p4=0, p5=135, sr=103, sw=0, l=0, gc=0 Response-Body-Transformed: Dechunked Producer: ModSecurity for Apache/2.9.5 (http://www.modsecurity.org/); OWASP_CRS/3.3.2. Server: Apache/2.4.52 (Ubuntu) Engine-Mode: "ENABLED" ..... ..... |
| [7] | General rules are provided and applied by default under the directory below. However maybe you need to customize them for your own web sites not to block necessary requests. |
|
root@www:~# ll /usr/share/modsecurity-crs/rules total 676 drwxr-xr-x 2 root root 4096 May 12 04:48 ./ drwxr-xr-x 4 root root 4096 May 12 04:48 ../ -rw-r--r-- 1 root root 13513 Aug 24 2021 REQUEST-901-INITIALIZATION.conf -rw-r--r-- 1 root root 13555 Aug 24 2021 REQUEST-903.9001-DRUPAL-EXCLUSION-RULES.conf -rw-r--r-- 1 root root 25812 Aug 24 2021 REQUEST-903.9002-WORDPRESS-EXCLUSION-RULES.conf -rw-r--r-- 1 root root 10642 Aug 24 2021 REQUEST-903.9003-NEXTCLOUD-EXCLUSION-RULES.conf -rw-r--r-- 1 root root 7822 Aug 24 2021 REQUEST-903.9004-DOKUWIKI-EXCLUSION-RULES.conf -rw-r--r-- 1 root root 1876 Aug 24 2021 REQUEST-903.9005-CPANEL-EXCLUSION-RULES.conf ..... ..... |
Matched Content