Kubernetes : Enable Dashboard2020/08/20 |
|
Enable Dashboard to manage Kubernetes Cluster on Web UI.
This example is based on the environment like follows.
-----------+---------------------------+--------------------------+------------
| | |
eth0|10.0.0.30 eth0|10.0.0.51 eth0|10.0.0.52
+----------+-----------+ +-----------+----------+ +-----------+----------+
| [ dlp.srv.world ] | | [ node01.srv.world ] | | [ node02.srv.world ] |
| Master Node | | Worker Node | | Worker Node |
+----------------------+ +----------------------+ +----------------------+
|
| [1] | Enable Dashboard on Master Node. |
|
root@dlp:~# kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.3/aio/deploy/recommended.yaml namespace/kubernetes-dashboard created serviceaccount/kubernetes-dashboard created service/kubernetes-dashboard created secret/kubernetes-dashboard-certs created secret/kubernetes-dashboard-csrf created secret/kubernetes-dashboard-key-holder created configmap/kubernetes-dashboard-settings created role.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created deployment.apps/kubernetes-dashboard created service/dashboard-metrics-scraper created deployment.apps/dashboard-metrics-scraper created |
| [2] | Add an account for Dashboard management. |
|
root@dlp:~#
kubectl create serviceaccount -n kubernetes-dashboard admin-user serviceaccount/admin-user created
root@dlp:~#
vi rbac.yml # create new apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: admin-user roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: admin-user namespace: kubernetes-dashboard
root@dlp:~#
kubectl apply -f rbac.yml clusterrolebinding.rbac.authorization.k8s.io/admin-user created # confirm security token of the account # it is the second column value on [token:] line root@dlp:~# kubectl -n kubernetes-dashboard describe secret $(kubectl -n kubernetes-dashboard get secret | grep admin-user | awk '{print $1}')
Name: admin-user-token-mfxbj
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: kubernetes.io/service-account.name: admin-user
kubernetes.io/service-account.uid: 0386627d-61be-4e49-b8a4-565eff4ab6cc
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 20 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlJnSUVrV0ZXUVM5WmpVX0hhbG9UaThaUG9lcGZf.....
# run kube-proxy root@dlp:~# kubectl proxy Starting to serve on 127.0.0.1:8001 # if access from other client hosts, set port-forwarding root@dlp:~# kubectl port-forward -n kubernetes-dashboard service/kubernetes-dashboard --address 0.0.0.0 10443:443 Forwarding from 0.0.0.0:10443 -> 8443 |
| [3] |
If you run [kubectl proxy], access to the URL below with an Web browser on Localhost.
⇒ http://localhost:8001/api/v1/namespaces/kubernetes-dashboard/services/https:kubernetes-dashboard:/proxy/
If you set port-fowarding, access to the URL below on a client computer in your local network.
⇒ https://(Master Node Hostname or IP address):(setting port)/
After displaying following form, Copy and paste the security token you confirmed on [2] to [Enter token] section and Click [Sing In] button.
|
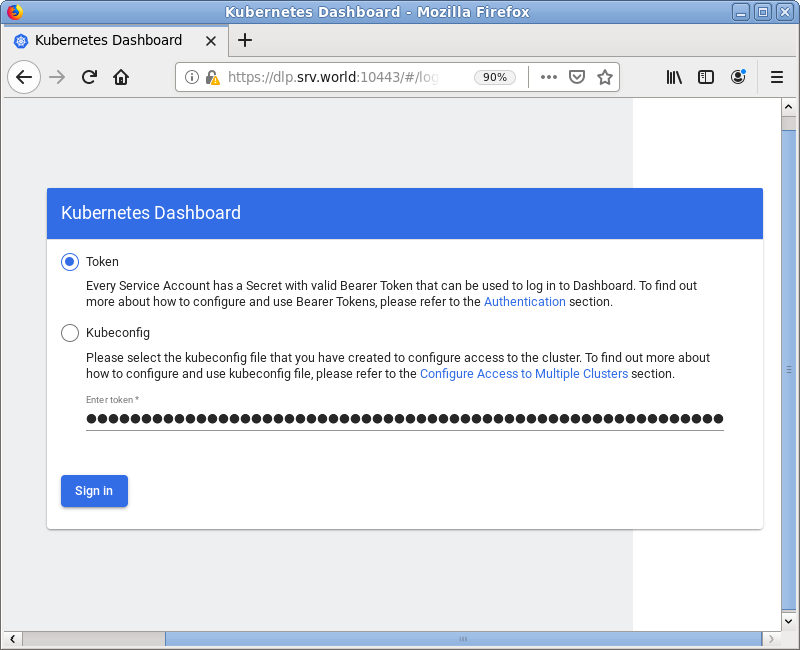
|
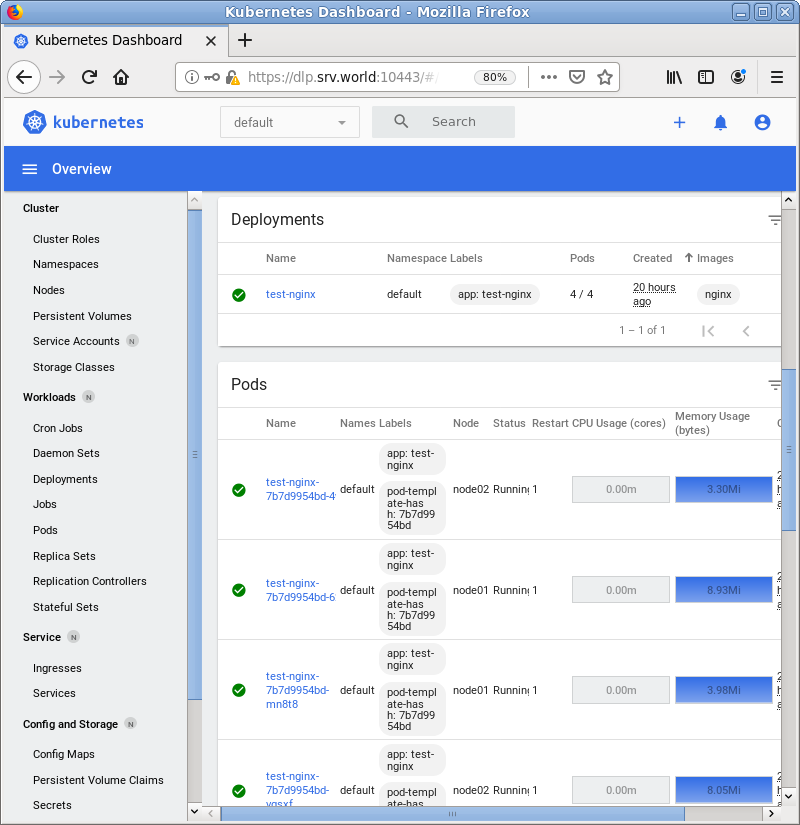
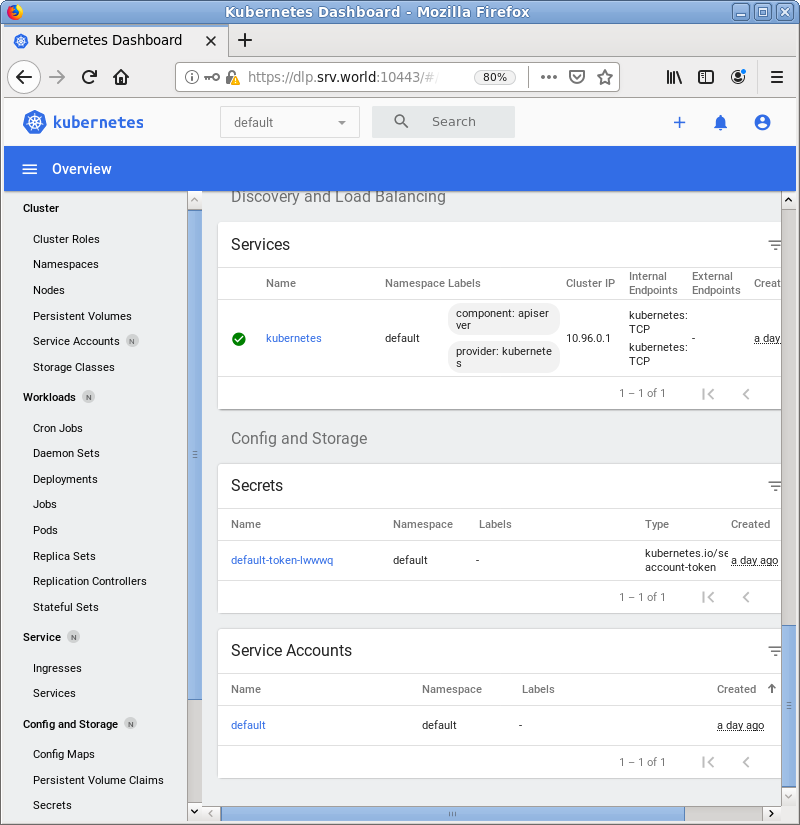
| [4] | After authentication successfully passed, Kubernetes Cluster Dashboard is displayed. The example screen below is the environment that Metrics Server also has been deployed. |
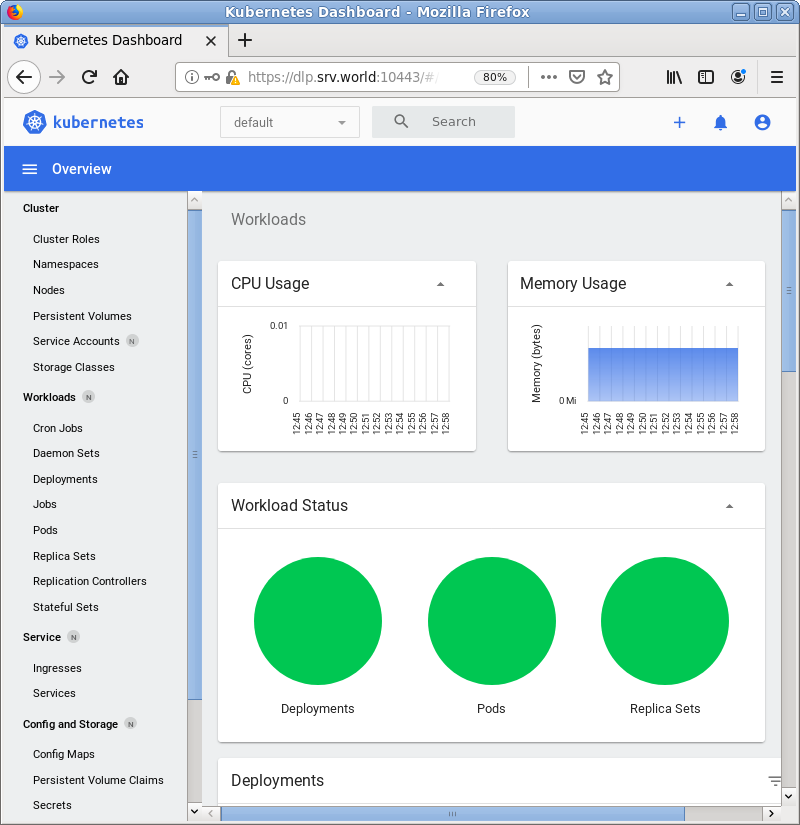
|
|
|
Matched Content