mod_security Settings2016/06/16 |
|
Use mod_security module to configure Web Application Firewall (WAF).
|
|
| [1] | Install mod_security. |
|
root@www:~# apt-get -y install libapache2-mod-security2
|
| [2] | After installing, security2 module has been enabled but security rules has not been set yet. It's possible to set rules to write them in ".conf" files under the directory which is specified on "IncludeOptional" parameter. |
|
root@www:~# grep -v -E '^?.#|^$' /etc/apache2/mods-available/security2.conf # possible to add rules in conf files under the /etc/modsecurity/
<IfModule security2_module>
SecDataDir /var/cache/modsecurity
IncludeOptional /etc/modsecurity/*.conf
</IfModule>
# rename sample file and enable it root@www:~# mv /etc/modsecurity/modsecurity.conf-recommended /etc/modsecurity/modsecurity.conf
root@www:~#
vi /etc/modsecurity/modsecurity.conf # default mode is "DetectionOnly" which does not block but only write logs # if turn to block mode, specify "SecRuleEngine On"
# -- Rule engine initialization ----------------------------------------------
# Enable ModSecurity, attaching it to every transaction. Use detection
# only to start with, because that minimises the chances of post-installation
# disruption.
#
SecRuleEngine DetectionOnly
.....
.....
# line 187: select part of logs to write
SecAuditLogParts ABJDEFHZ
### available audit log parts
A: audit log header (mandatory) B: request log headers C: request body D: reserved for intermediary response headers (not implemented yet) E: intermediary response body F: final response headers G: reserved for the actual response body (not implemented) H: audit log trailer I: this part is a replacement for part C but except multipart/form-data encoding J: this part contains information about the files uploaded using multipart/form-data encoding K: this part contains a full list of every rule that matched (one per line) in the order they were matched Z: final boundary, signifies the end of the entry (mandatory) |
| [3] |
It's possible to write a rule like follows.
⇒ SecRule VARIABLES OPERATOR [ACTIONS]
Each parameter has many kind of values, refer to official documents below.
https://github.com/SpiderLabs/ModSecurity/wiki/Reference-Manual |
| [4] | For Exmaple, set some rules and verify it works normally. |
|
root@www:~#
vi /etc/modsecurity/rules-01.conf # default action when matching rules SecDefaultAction "phase:2,deny,log,status:406" # "etc/passwd" is included in request URI SecRule REQUEST_URI "etc/passwd" "id:'500001'" # "../" is included in request URI SecRule REQUEST_URI "\.\./" "id:'500002'" # "<SCRIPT" is included in arguments SecRule ARGS "<[Ss][Cc][Rr][Ii][Pp][Tt]" "id:'500003'" # "SELECT FROM" is included in arguments SecRule ARGS "[Ss][Ee][Ll][Ee][Cc][Tt][[:space:]]+[Ff][Rr][Oo][Mm]" "id:'500004'" systemctl restart apache2
|
| [5] | Access to the URI which includes words you set and verify it works normally. |
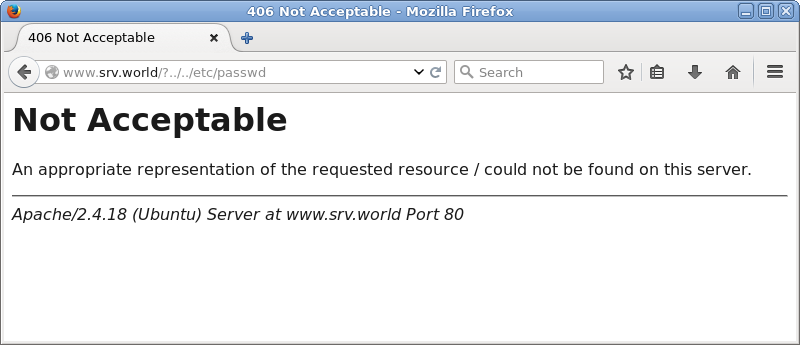
|
| [6] | The logs for mod_security is placed in the directory like follows. |
|
root@www:~# cat /var/log/apache2/modsec_audit.log --b679270f-A-- [17/Jun/2016:11:56:26 +0900] V2Nm2goAAB8AAAurUwAAAAAA 10.0.0.18 56003 10.0.0.31 80 --b679270f-B-- GET /?../../etc/passwd HTTP/1.1 Host: www.srv.world User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:38.0) Gecko/20100101 Firefox/38.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: keep-alive --b679270f-F-- HTTP/1.1 406 Not Acceptable Content-Length: 330 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html; charset=iso-8859-1 ..... ..... |
Matched Content