Kerberos Authentication2016/06/13 |
|
Limit accesses on specific web pages and use Windows Active Directory users for authentication with SSL connection.
It's necessarry to be running
Windows Active Directory in your LAN.
This example based on the environment below.
|
|||||||||
| [1] | For example, set Kerberos Authentication under the directory [/var/www/html/auth-kerberos] and also set to be required SSL connection. |
|
root@www:~#
apt-get -y install libapache2-mod-auth-kerb # specify Realm +------------------+ Configuring Kerberos Authentication +------------------+ | When users attempt to use Kerberos and specify a principal or user name | | without specifying what administrative Kerberos realm that principal | | belongs to, the system appends the default realm. The default realm may | | also be used as the realm of a Kerberos service running on the local | | machine. Often, the default realm is the uppercase version of the local | | DNS domain. | | | | Default Kerberos version 5 realm: | | | | SRV.WORLD________________________________________________________________ | | | | <Ok> | | | +---------------------------------------------------------------------------+ # specify Active Directory's hostname +------------------+ Configuring Kerberos Authentication +------------------+ | Enter the hostnames of Kerberos servers in the FD3S.SRV.WORLD Kerberos | | realm separated by spaces. | | | | Kerberos servers for your realm: | | | | fd3s.srv.world___________________________________________________________ | | | | <Ok> | | | +---------------------------------------------------------------------------+ # specify Active Directory's hostname +------------------+ Configuring Kerberos Authentication +------------------+ | Enter the hostname of the administrative (password changing) server for | | the FD3S.SRV.WORLD Kerberos realm. | | | | Administrative server for your Kerberos realm: | | | | fd3s.srv.world___________________________________________________________ | | | | <Ok> | | | +---------------------------------------------------------------------------+ # create keytab HTTP/[AD's hostname or IP address]@[Realm name] root@www:~# echo "HTTP/fd3s.srv.world@SRV.WORLD" > /etc/krb5.keytab
root@www:~#
vi /etc/apache2/sites-available/auth-kerberos.conf # create new
<Directory /var/www/html/auth-kerberos>
SSLRequireSSL
AuthType Kerberos
AuthName "Kerberos Authntication"
KrbAuthRealms SRV.WORLD
Krb5Keytab /etc/krb5.keytab
KrbMethodNegotiate Off
KrbSaveCredentials Off
KrbVerifyKDC Off
Require valid-user
</Directory>
mkdir /var/www/html/auth-kerberos root@www:~# a2ensite auth-kerberos Enabling site auth-kerberos. To activate the new configuration, you need to run: service apache2 reload
root@www:~#
systemctl restart apache2
# create a test page
root@www:~#
vi /var/www/html/auth-kerberos/index.html <html> <body> <div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;"> Test Page for Kerberos Auth </div> </body> </html> |
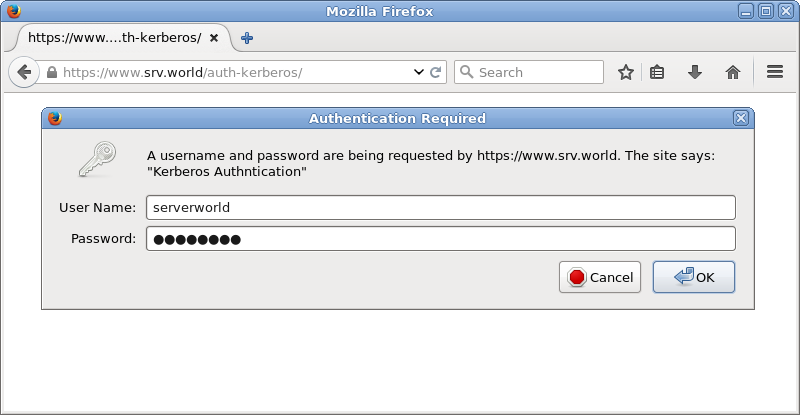
| [2] | Access to the test page from a client computer with web browser. Then authentication is required like follows as a setting, answer with a user which is added in Active Directory. |
|
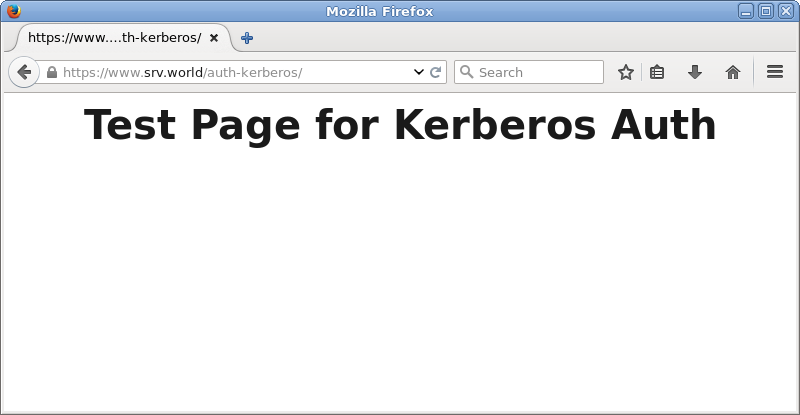
| [3] | Just accessed. |
|
Matched Content