OpenSSH : SSH Key-Pair Authentication2023/12/19 |
|
Configure SSH server to login with Key-Pair Authentication.
Create a private key for client and a public key for server to do it. |
|
| [1] | Create Key-Pair by each user, so login with a common user on SSH Server Host and work like follows. |
|
# create key-pair freebsd@dlp:~ $ ssh-keygen Generating public/private rsa key pair. Enter file in which to save the key (/home/freebsd/.ssh/id_rsa): # Enter or input changes if you want Enter passphrase (empty for no passphrase): # set passphrase (if set no passphrase, Enter with empty) Enter same passphrase again: Your identification has been saved in /home/freebsd/.ssh/id_rsa Your public key has been saved in /home/freebsd/.ssh/id_rsa.pub The key fingerprint is: SHA256:uNTwILz1kwqxTKplnlSWcxqEIB0mZQlyERz2wRML1yE freebsd@dlp.srv.world The key's randomart image is: ..... .....freebsd@dlp:~ $ ls -l ~/.ssh total 18 -rw------- 1 freebsd freebsd 2655 Dec 19 10:36 id_rsa -rw-r--r-- 1 freebsd freebsd 575 Dec 19 10:36 id_rsa.pub -rw------- 1 freebsd freebsd 846 Dec 19 10:12 known_hosts -rw-r--r-- 1 freebsd freebsd 98 Dec 19 10:12 known_hosts.oldfreebsd@dlp:~ $ mv ~/.ssh/id_rsa.pub ~/.ssh/authorized_keys |
| [2] | Transfer the private key created on the Server to a Client, then it's possible to login with Key-Pair authentication. |
|
freebsd@node01:~ $
mkdir ~/.ssh freebsd@node01:~ $ chmod 700 ~/.ssh
# transfer the private key to the local ssh directory freebsd@node01:~ $ scp freebsd@dlp.srv.world:/home/freebsd/.ssh/id_rsa ~/.ssh/ (freebsd@dlp.srv.world) Password for freebsd@dlp.srv.world: id_rsa 100% 2655 2.8MB/s 00:00freebsd@node01:~ $ ssh freebsd@dlp.srv.world Enter passphrase for key '/home/freebsd/.ssh/id_rsa': # passphrase if you set Last login: Tue Dec 19 10:01:15 2023 from 10.0.0.250 FreeBSD 14.0-RELEASE (GENERIC) #0 releng/14.0-n265380-f9716eee8ab4: Fri Nov 10 05:57:23 UTC 2023 Welcome to FreeBSD! ..... ..... freebsd@dlp:~ $ # logined |
| [3] | If you set [PasswordAuthentication no], it's more secure. |
|
root@dlp:~ #
vi /etc/ssh/sshd_config # line 61 : uncomment PasswordAuthentication no # line 65 : uncomment and change KbdInteractiveAuthentication no
service sshd restart |
|
SSH Key-Pair Authentication on Windows Client #1
|
|
This is the example to login to SSH server from Windows Client.
On this example, it shows with Putty. Before it, Transfer a private key to Windows client computer. |
|
| [4] |
Run [Puttygen.exe] that is included in [Putty]. (placed in the folder [Putty.exe] is also placed) If not included, Download it from official site (www.chiark.greenend.org.uk/~sgtatham/putty/). After starting [Puttygen.exe], Click [Load] button on the following window. |
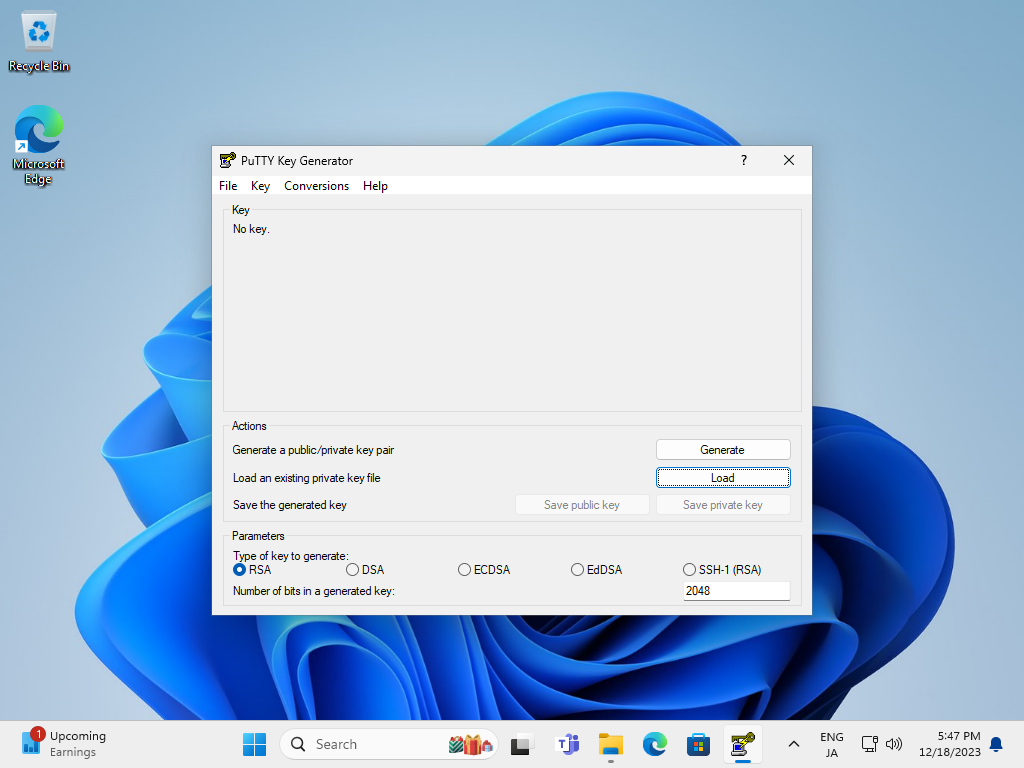
|
| [5] | Specify the private key that you transferred from SSH server, then passphrase is required like follows, answer it. (if not set passphrase, this step is skipped) |
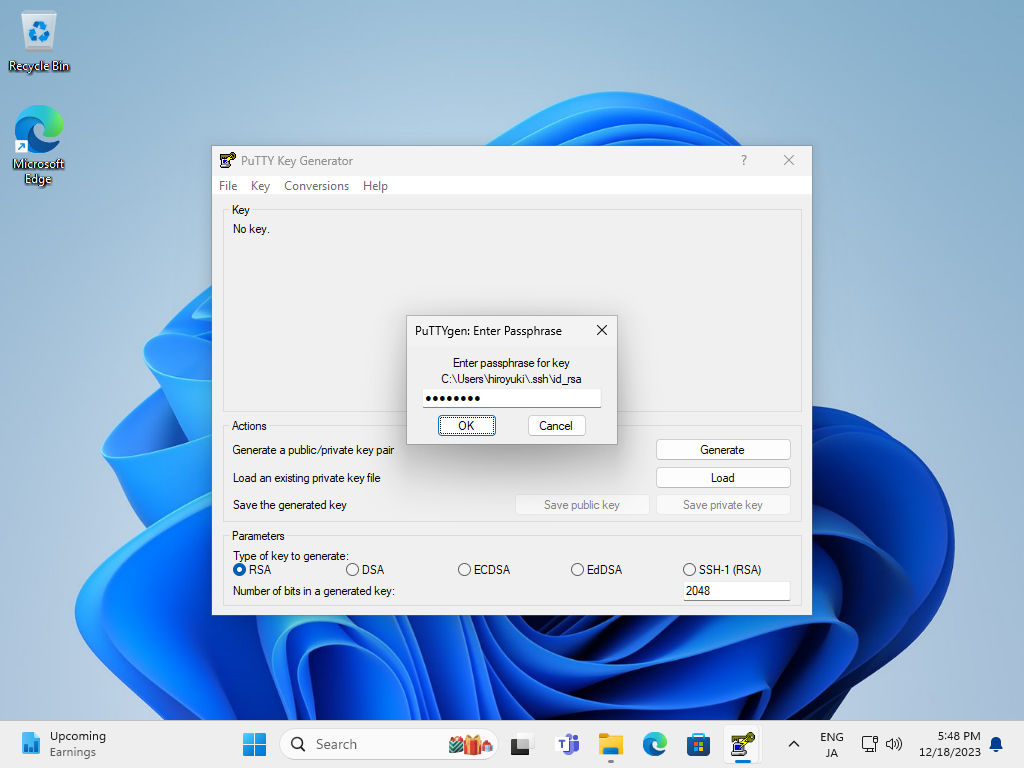
|
| [6] | Click [Save private key] button to save it under a folder you like with any file name you like. |
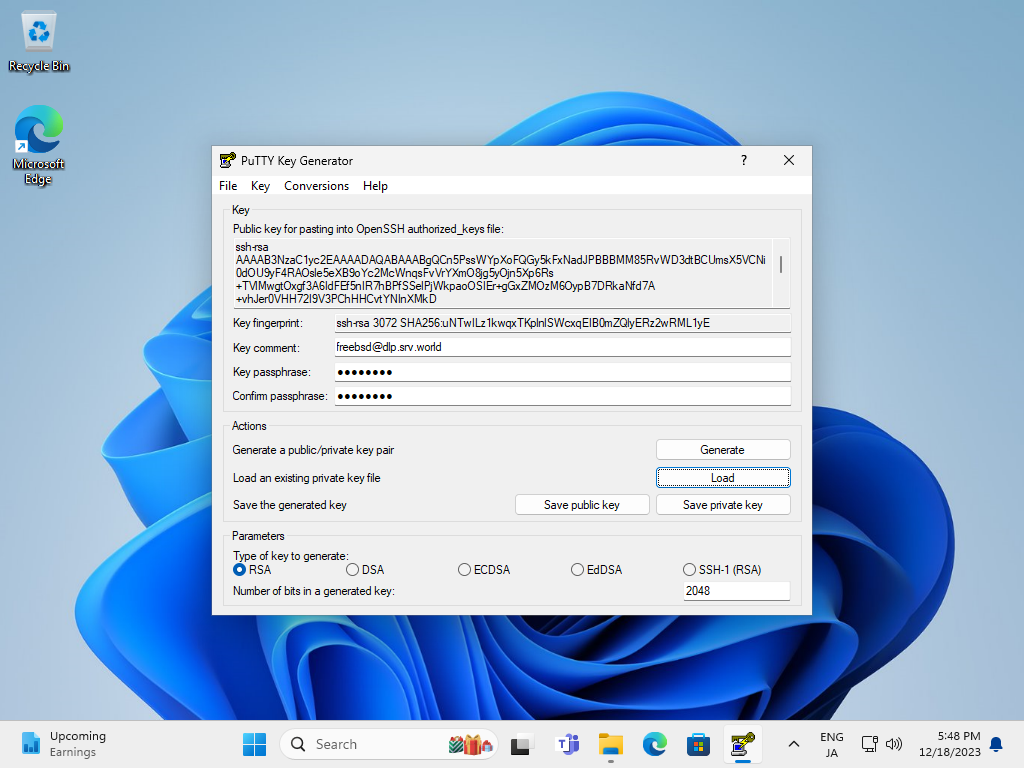
|
| [7] | Start Putty and Open [Connection] - [SSH] - [Auth] - [Credencials] on the left pane, then specify your private key on the [Private key file] field. |
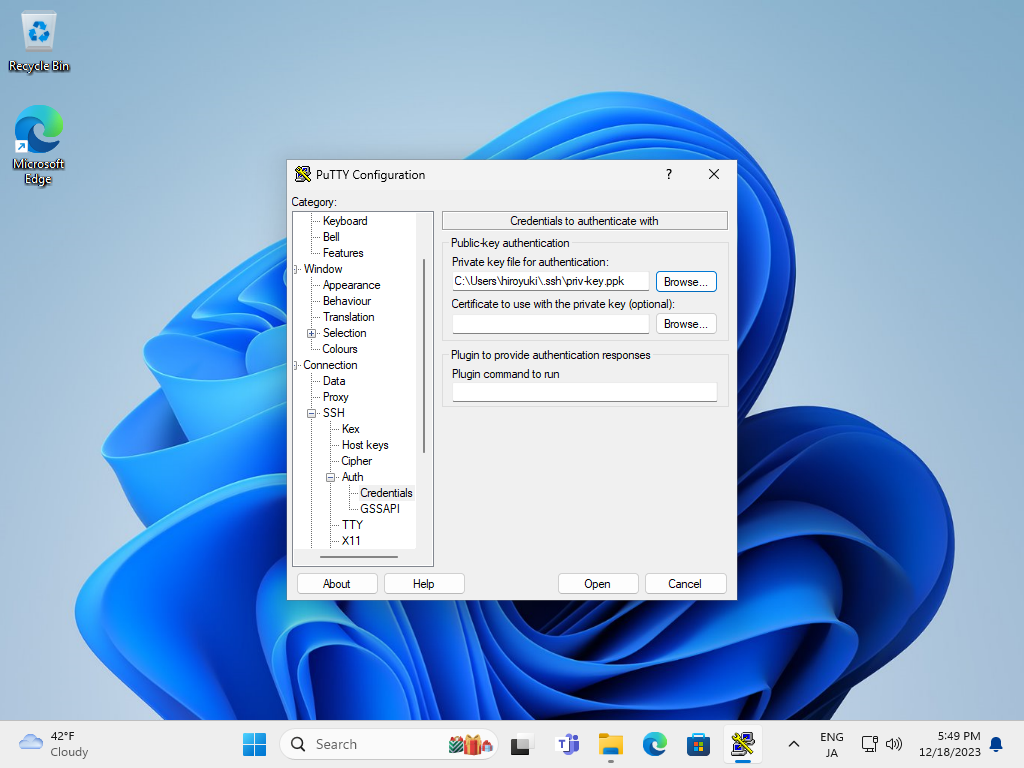
|
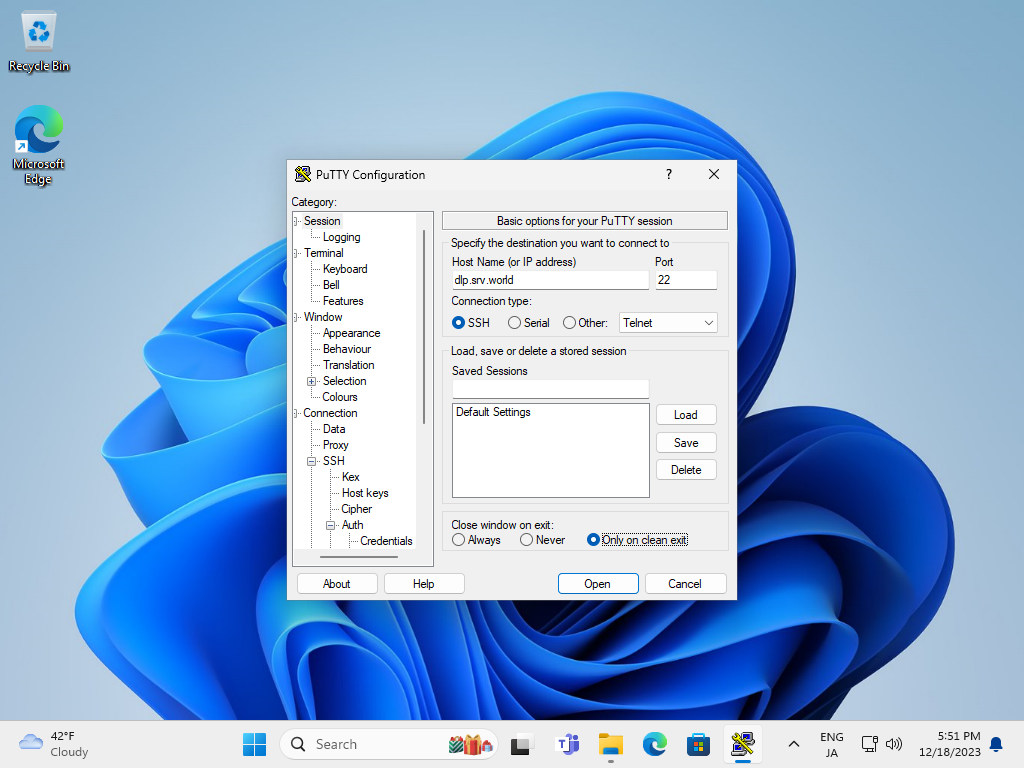
| [8] | Back to the [Session] on the left pane and specify your SSH server host to Connect. |
|
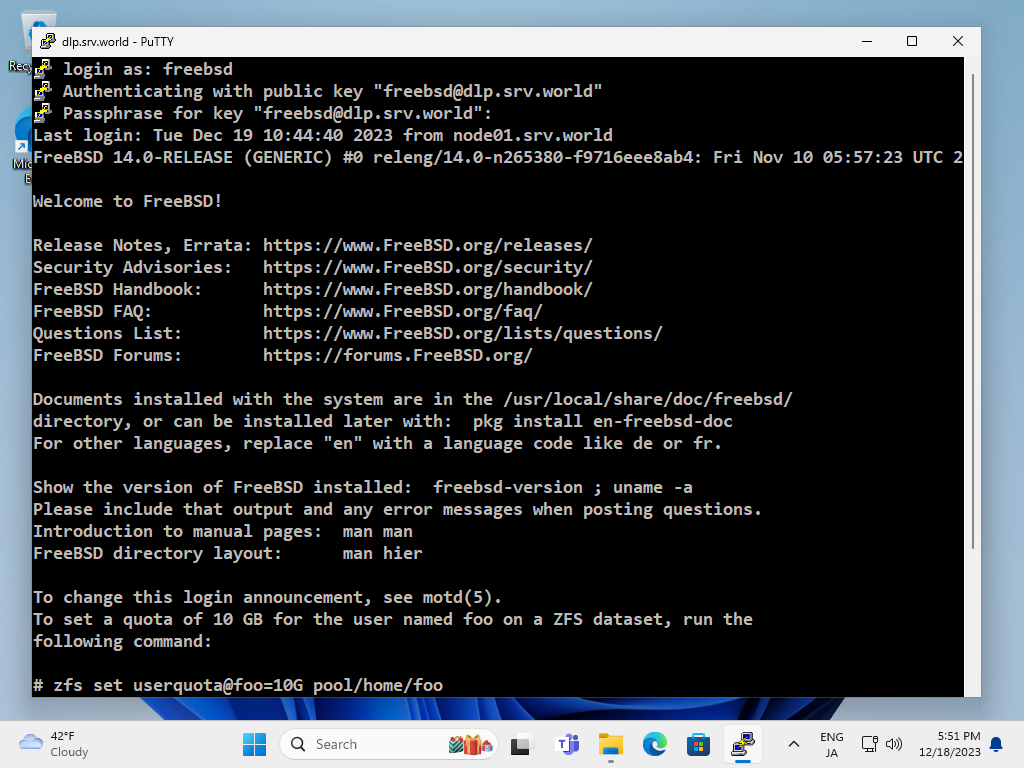
| [9] | When SSH key-pair is set, the passphrase if it is set is required to login like follows, then answer it. |
|
|
SSH Key-Pair Authentication on Windows #2
|
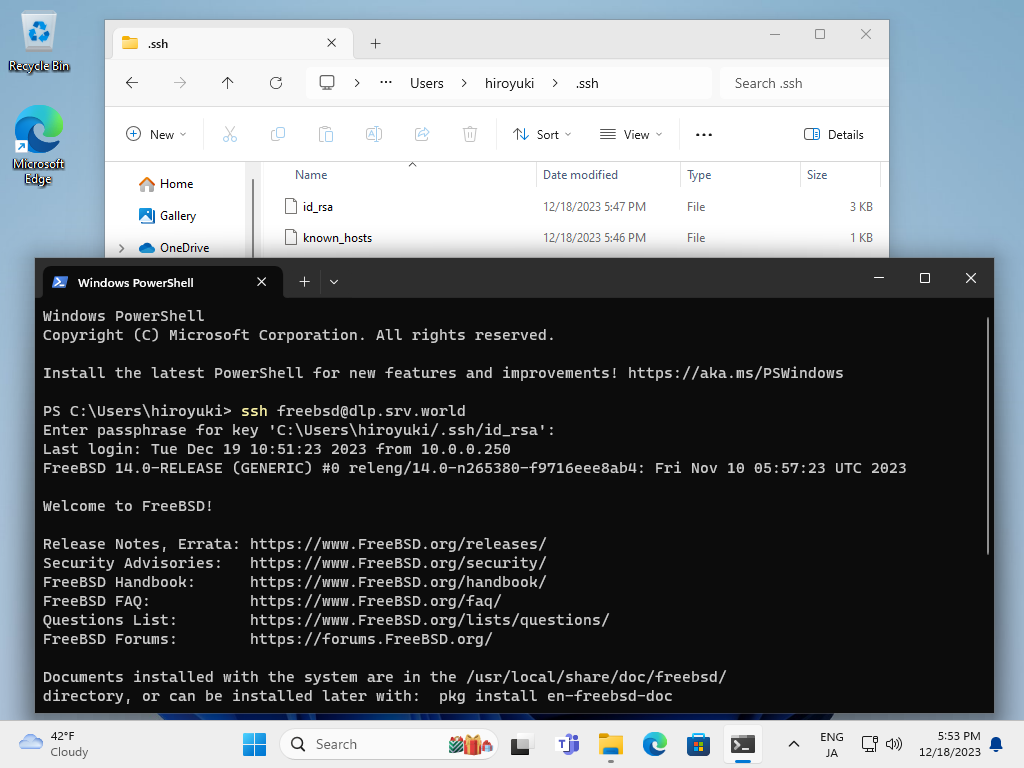
| [10] | OpenSSH Client has been implemented as an Windows feature, so it's possible to authenticate with SSH Key-Pair without Putty and other 3rd party softwares. Transfer your private key to your Windows and put it under the [(logon user home).ssh] folder like follows, then it's ready to use Key-Pair authentication. |
|
Matched Content