Join in Active Directory Domain2023/02/23 |
|
Join in Windows Active Directory Domain.
This tutorial needs Windows Active Directory Domain Service in your Local Network.
This example is based on the environment like follows.
|
|||||||||||
| [1] |
Set Time Synchronization between ESXi Host and Active Directory Host.
* ESXi has UTC timezone, so display time dose not match, though |
||||||||||
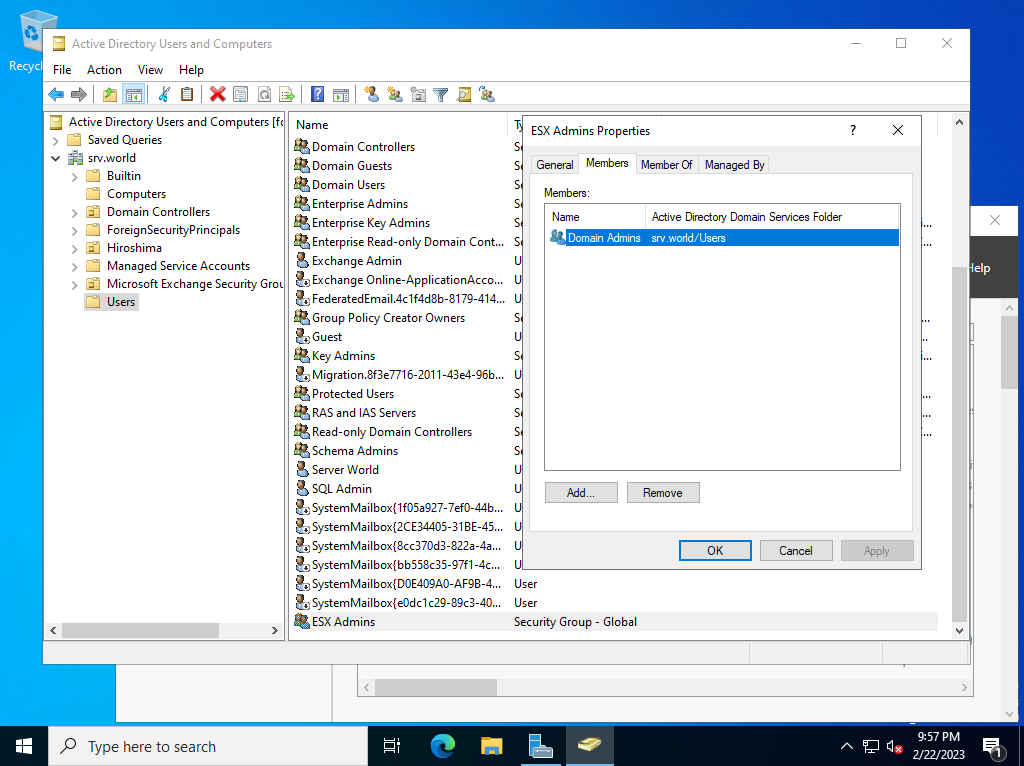
| [2] | Create a group named [ESX Admins] for ESXi on Active Directory. You can add any member to it. It adds [Domain Admins] on this example. |
|
| [3] | To configure on shell access, set like follows. |
|
# change DNS setting to refer to AD [root@ctrl:~] esxcli network ip dns server list DNSServers: 10.0.0.10[root@ctrl:~] esxcli network ip dns server add --server=10.0.0.100 [root@ctrl:~] esxcli network ip dns server remove --server=10.0.0.10 [root@ctrl:~] esxcli network ip dns server list DNSServers: 10.0.0.100 # start required service [root@ctrl:~] /etc/init.d/lwsmd start Starting Likewise Service Manager [memory reservation set] SUCCESS [starting lsass service] Starting service dependency: netlogon Starting service dependency: lwio Starting service dependency: rdr Starting service: lsass ...ok
[root@ctrl:~]
chkconfig lwsmd on
# allow firewall rules for AD (rules are added by default) # * default firewall rules on ESXi are set denied even for outbound [root@ctrl:~] esxcli network firewall ruleset set -r activeDirectoryAll --enabled 1 [root@ctrl:~] esxcli network firewall ruleset list | grep -i active activeDirectoryAll true[root@ctrl:~] esxcli network firewall ruleset rule list | grep -i active activeDirectoryAll Outbound UDP Dst 88 88 activeDirectoryAll Outbound TCP Dst 88 88 activeDirectoryAll Outbound UDP Dst 123 123 activeDirectoryAll Outbound UDP Dst 137 137 activeDirectoryAll Outbound TCP Dst 139 139 activeDirectoryAll Outbound TCP Dst 389 389 activeDirectoryAll Outbound UDP Dst 389 389 activeDirectoryAll Outbound TCP Dst 445 445 activeDirectoryAll Outbound UDP Dst 464 464 activeDirectoryAll Outbound TCP Dst 464 464 activeDirectoryAll Outbound TCP Dst 3268 3268 activeDirectoryAll Outbound TCP Dst 7476 7476 activeDirectoryAll Inbound TCP Dst 2020 2020 # join in Active Directory domain # /usr/lib/vmware/likewise/bin/domainjoin-cli join (AD domain name) (AD domain username) [root@ctrl:~] /usr/lib/vmware/likewise/bin/domainjoin-cli join srv.world Serverworld Joining to AD Domain: srv.world With Computer DNS Name: ctrl.srv.world Serverworld@SRV.WORLD's password: SUCCESS # after joining to Active Directory, # it grants admin privilege to [ESX Admins] group [root@ctrl:~] esxcli system permission list Principal Is Group Role Role Description ----------------- -------- ----- ---------------- FD3S01\esx^admins true Admin Full access rights dcui false Admin Full access rights root false Admin Full access rights vpxuser false Admin Full access rights |
| [4] | Verify to access to ESXi Host with any AD user who is in [ESX Admins] group from any client computer. |
|
[root@localhost ~]# ssh serverworld@srv.world@ctrl.srv.world (serverworld@srv.world@ctrl.srv.world) Password: The time and date of this login have been sent to the system logs. WARNING: All commands run on the ESXi shell are logged and may be included in support bundles. Do not provide passwords directly on the command line. Most tools can prompt for secrets or accept them from standard input. VMware offers supported, powerful system administration tools. Please see www.vmware.com/go/sysadmintools for details. The ESXi Shell can be disabled by an administrative user. See the vSphere Security documentation for more information. Could not chdir to home directory /home/local/FD3S01/serverworld: No such file or directory [FD3S01\serverworld@ctrl:~] |
|
To join in Active Directory Domain on VMware Host Client, Configure like follows.
|
|
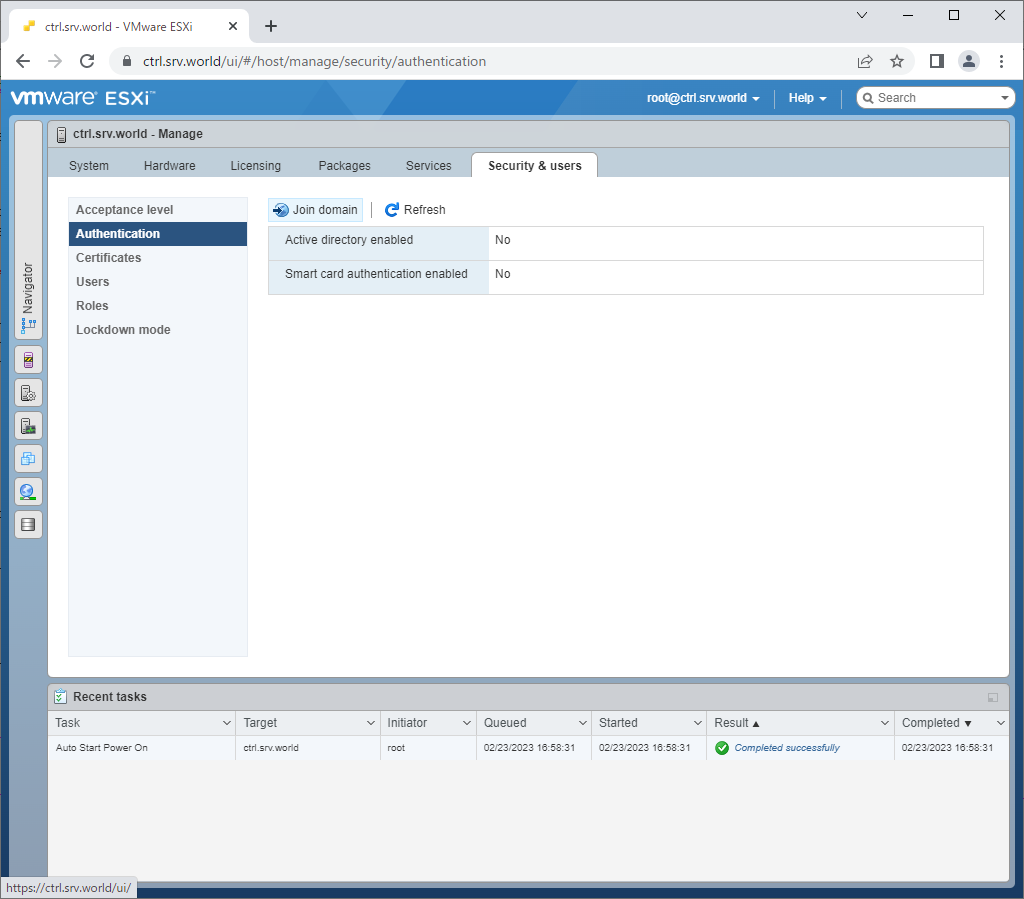
| [5] | Login to VMware Host Client with root user account and click [Manage] icon that is under [Navigator] menu. Next, move to [Security & users] tab and then, click [Join domain] button. |
|
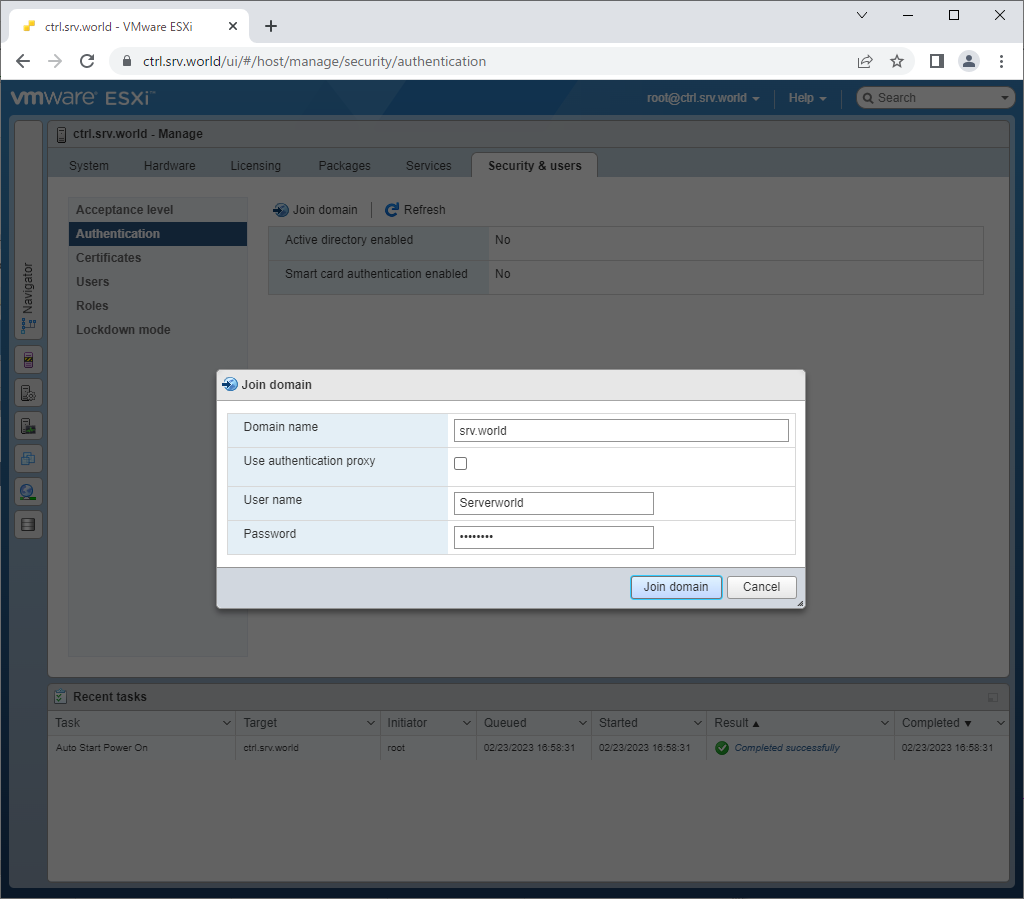
| [6] | Input required information and click [Join domain] button. Required service and firewall rules are automatically configured unlike commands operation. |
|
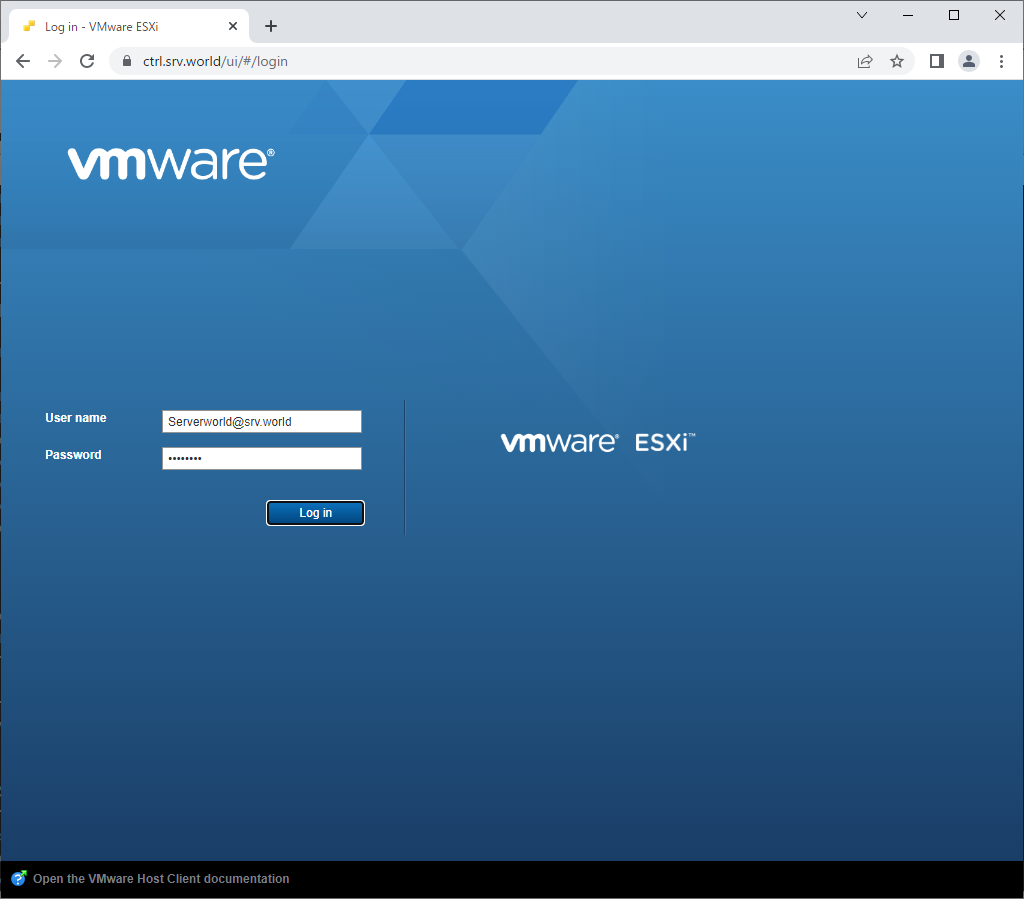
| [7] | After joining to Active Directory, verify to access to VMware Host Client with any AD user who is in [ESX Admins] group. |
|
|
Matched Content