OpenSCAP : Install2022/07/01 |
|
Install OpenSCAP which is the security audit and vulnerability scanning tool based on SCAP (Security Content Automation Protocol).
For details about SCAP, refer to the site below.
⇒ https://csrc.nist.gov/projects/security-content-automation-protocol OVAL (Open Vulnerability and Assessment Language) XCCDF (Extensible Configuration Checklist Description Format) OCIL (Open Checklist Interactive Language) CPE (Common Platform Enumeration) CCE (Common Configuration Enumeration) CVE (Common Vulnerabilities and Exposures) CVSS (Common Vulnerability Scoring System) |
|
| [1] | Install OpenSCAP command line tool and SCAP Security Guide for Linux. |
|
[root@dlp ~]# dnf -y install openscap-scanner scap-security-guide
|
| [2] | SCAP Security Guide is installed under the [/usr/share/xml/scap/ssg/content] directory. |
|
[root@dlp ~]# ll /usr/share/xml/scap/ssg/content/ total 41804 -rw-r--r--. 1 root root 21300553 Jun 2 00:13 ssg-cs9-ds.xml -rw-r--r--. 1 root root 21502789 Jun 2 00:13 ssg-rhel9-ds.xml # display description for each content [root@dlp ~]# oscap info /usr/share/xml/scap/ssg/content/ssg-cs9-ds.xml
Document type: Source Data Stream
Imported: 2022-06-02T00:13:16
Stream: scap_org.open-scap_datastream_from_xccdf_ssg-rhel9-xccdf-1.2.xml
Generated: (null)
Version: 1.3
Checklists:
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-xccdf-1.2.xml
Status: draft
Generated: 2022-06-01
Resolved: true
Profiles:
Title: ANSSI-BP-028 (enhanced)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_enhanced
Title: ANSSI-BP-028 (high)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_high
Title: ANSSI-BP-028 (intermediary)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_intermediary
Title: ANSSI-BP-028 (minimal)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_minimal
Title: [DRAFT] CIS Red Hat Enterprise Linux 9 Benchmark for Level 2 - Server
Id: xccdf_org.ssgproject.content_profile_cis
Title: [DRAFT] CIS Red Hat Enterprise Linux 9 Benchmark for Level 1 - Server
Id: xccdf_org.ssgproject.content_profile_cis_server_l1
Title: [DRAFT] CIS Red Hat Enterprise Linux 9 Benchmark for Level 1 - Workstation
Id: xccdf_org.ssgproject.content_profile_cis_workstation_l1
Title: [DRAFT] CIS Red Hat Enterprise Linux 9 Benchmark for Level 2 - Workstation
Id: xccdf_org.ssgproject.content_profile_cis_workstation_l2
Title: [DRAFT] Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171)
Id: xccdf_org.ssgproject.content_profile_cui
Title: Australian Cyber Security Centre (ACSC) Essential Eight
Id: xccdf_org.ssgproject.content_profile_e8
Title: Health Insurance Portability and Accountability Act (HIPAA)
Id: xccdf_org.ssgproject.content_profile_hipaa
Title: Australian Cyber Security Centre (ACSC) ISM Official
Id: xccdf_org.ssgproject.content_profile_ism_o
Title: [DRAFT] Protection Profile for General Purpose Operating Systems
Id: xccdf_org.ssgproject.content_profile_ospp
Title: PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 9
Id: xccdf_org.ssgproject.content_profile_pci-dss
Title: [DRAFT] DISA STIG for Red Hat Enterprise Linux 9
Id: xccdf_org.ssgproject.content_profile_stig
Title: [DRAFT] DISA STIG with GUI for Red Hat Enterprise Linux 9
Id: xccdf_org.ssgproject.content_profile_stig_gui
Referenced check files:
ssg-rhel9-oval.xml
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
ssg-rhel9-ocil.xml
system: http://scap.nist.gov/schema/ocil/2
security-data-oval-com.redhat.rhsa-RHEL9.xml.bz2
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
Checks:
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-oval.xml
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-ocil.xml
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-cpe-oval.xml
Ref-Id: scap_org.open-scap_cref_security-data-oval-com.redhat.rhsa-RHEL9.xml.bz2
Dictionaries:
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-cpe-dictionary.xml
|
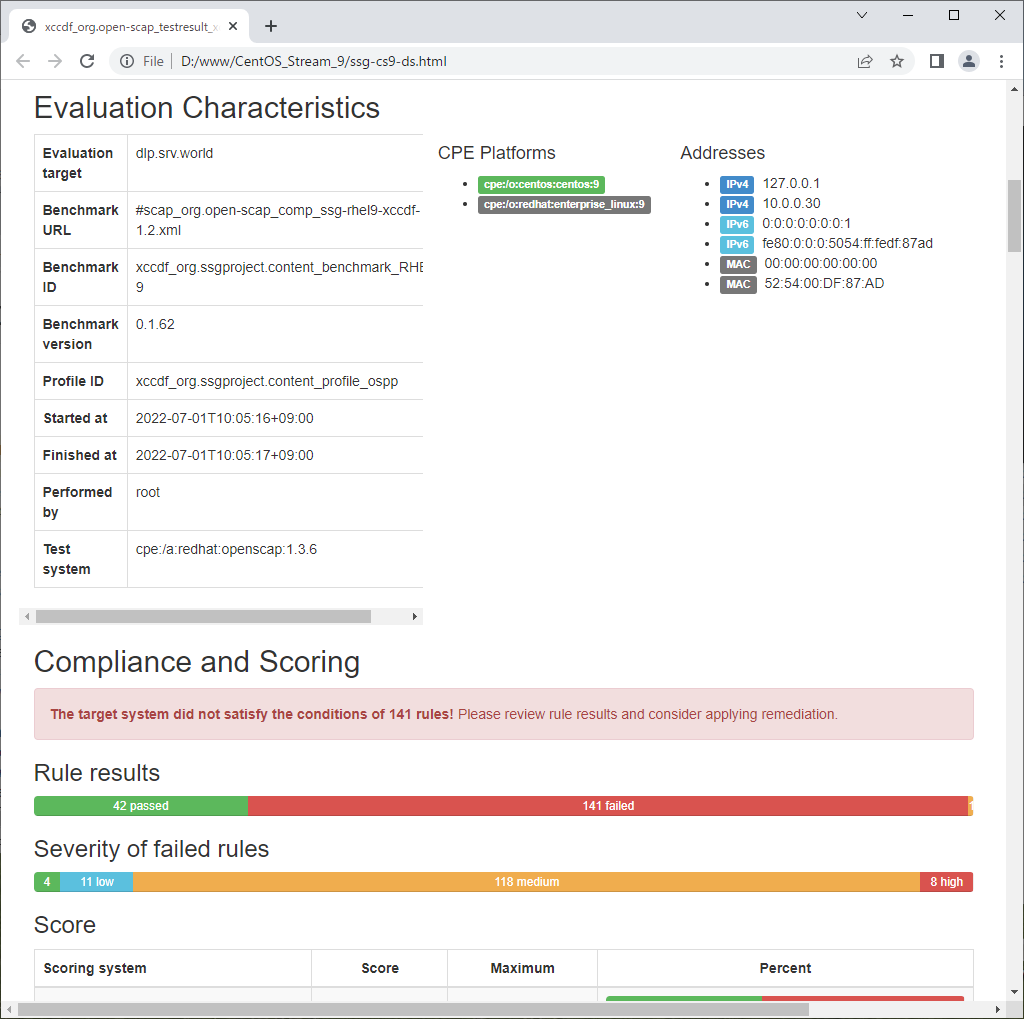
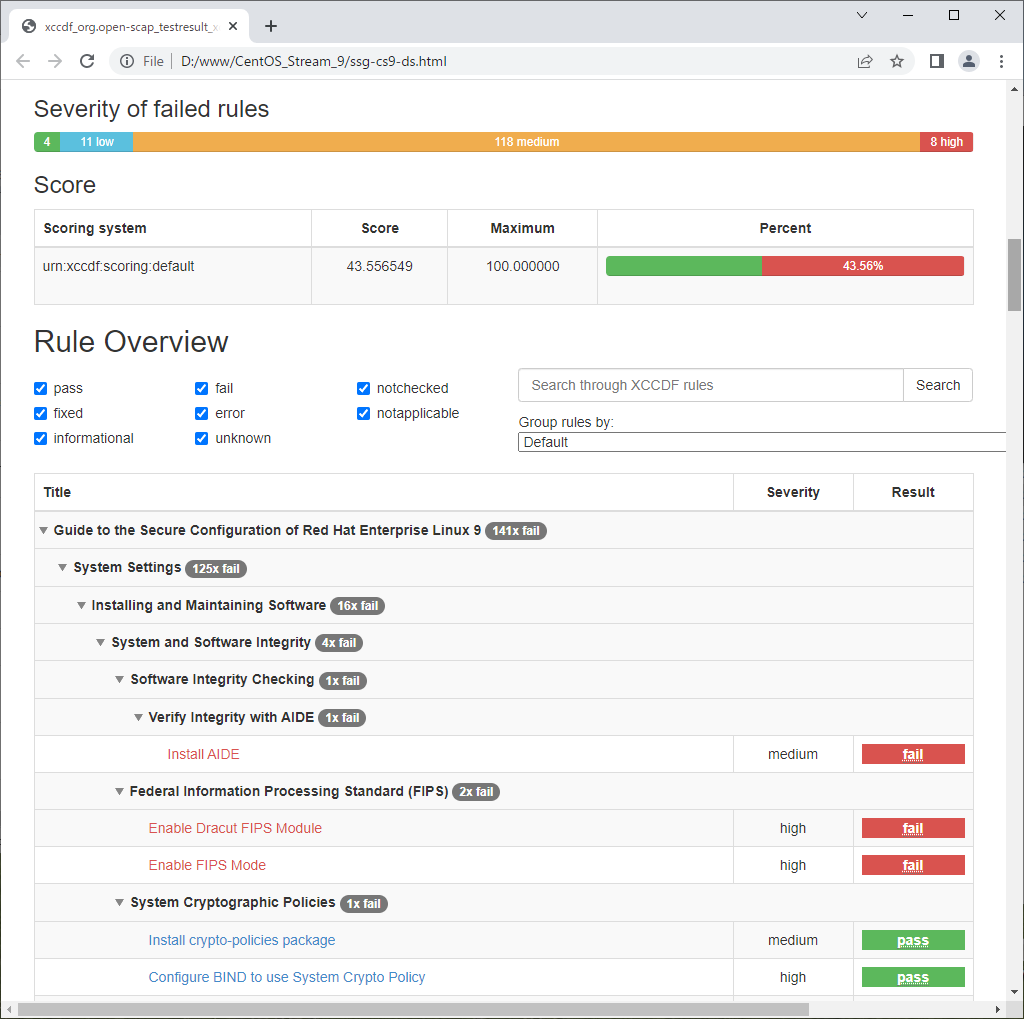
| [3] | Scan CentOS System with [oscap] command. Scan result is renerated as HTML report, you should verify it and try to apply recommended settings as much as possible. |
|
# xccdf : specify [xccdf] module
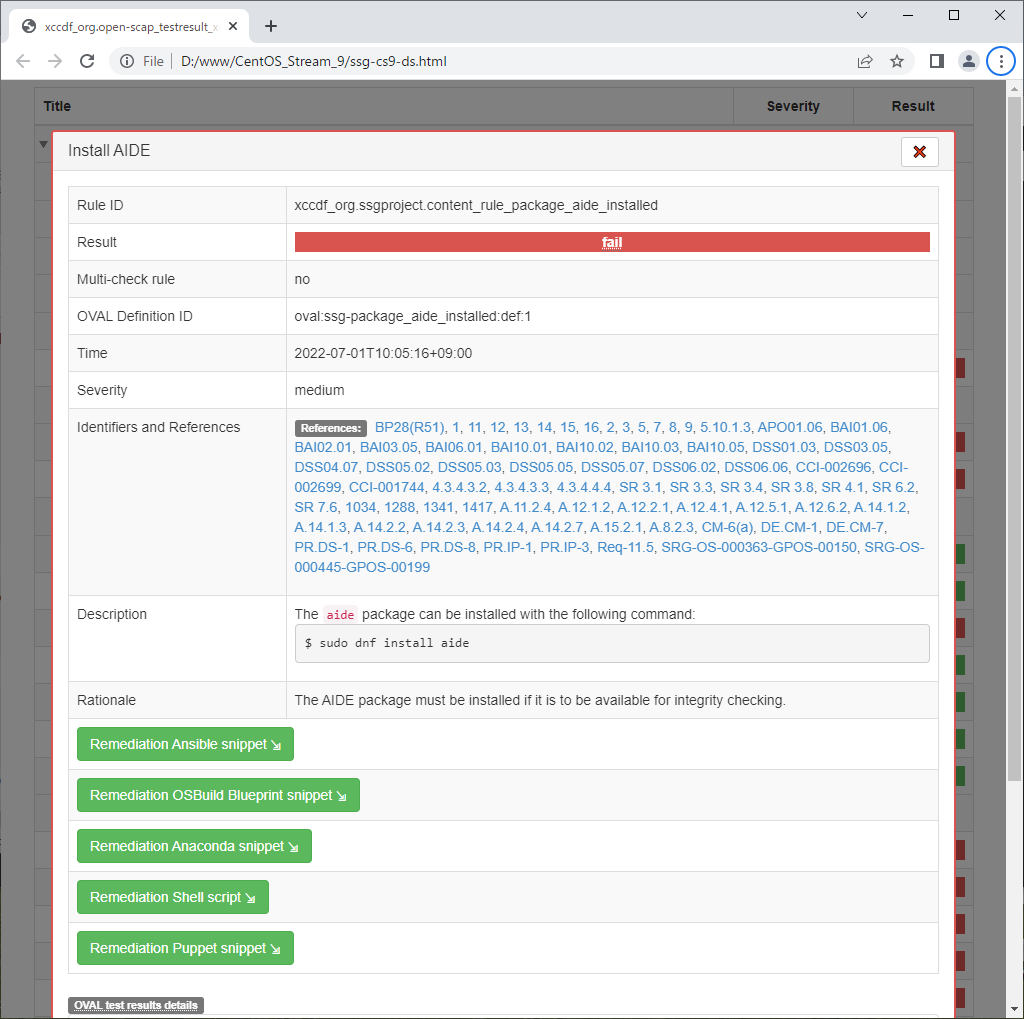
# ⇒ available modules : info, xccdf, oval, ds, cpe, cvss, cve, cvrf # [--profile] : specify profile # ⇒ available profiles are on the result you run [oscap info] command above # [--results] : output file # [--report] : output HTML report oscap xccdf eval \ --profile xccdf_org.ssgproject.content_profile_ospp \ --results ssg-cs9-ds.xml \ --report ssg-cs9-ds.html \ /usr/share/xml/scap/ssg/content/ssg-cs9-ds.xml Downloading: https://access.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml.bz2 ... ok --- Starting Evaluation --- Title Install AIDE Rule xccdf_org.ssgproject.content_rule_package_aide_installed Result fail Title Enable Dracut FIPS Module Rule xccdf_org.ssgproject.content_rule_enable_dracut_fips_module Result fail Title Enable FIPS Mode Rule xccdf_org.ssgproject.content_rule_enable_fips_mode Result fail Title Install crypto-policies package Rule xccdf_org.ssgproject.content_rule_package_crypto-policies_installed Result pass Title Configure BIND to use System Crypto Policy Rule xccdf_org.ssgproject.content_rule_configure_bind_crypto_policy Result pass Title Configure System Cryptography Policy Rule xccdf_org.ssgproject.content_rule_configure_crypto_policy Result fail Title Configure Kerberos to use System Crypto Policy Rule xccdf_org.ssgproject.content_rule_configure_kerberos_crypto_policy Result pass ..... ..... |

|
|
|
|
| [4] |
It's possible to generate remediation script from scaned result.
Remediation script will change various system settings, so you must take care if you run it, especially for production systems.
|
|
# make sure the [Result ID] in the result output on [3] [root@dlp ~]# oscap info ssg-cs9-ds.xml | grep "Result ID"
Result ID: xccdf_org.open-scap_testresult_xccdf_org.ssgproject.content_profile_ospp
# generate remediation script
# [--fix-type] : specify fix type : default is Bash # ⇒ available type ⇒ bash, ansible, puppet, anaconda, ignition, kubernetes, blueprint # [--output] : specify output script file # [--result-id] : specify [Result ID]
[root@dlp ~]#
[root@dlp ~]# oscap xccdf generate fix \
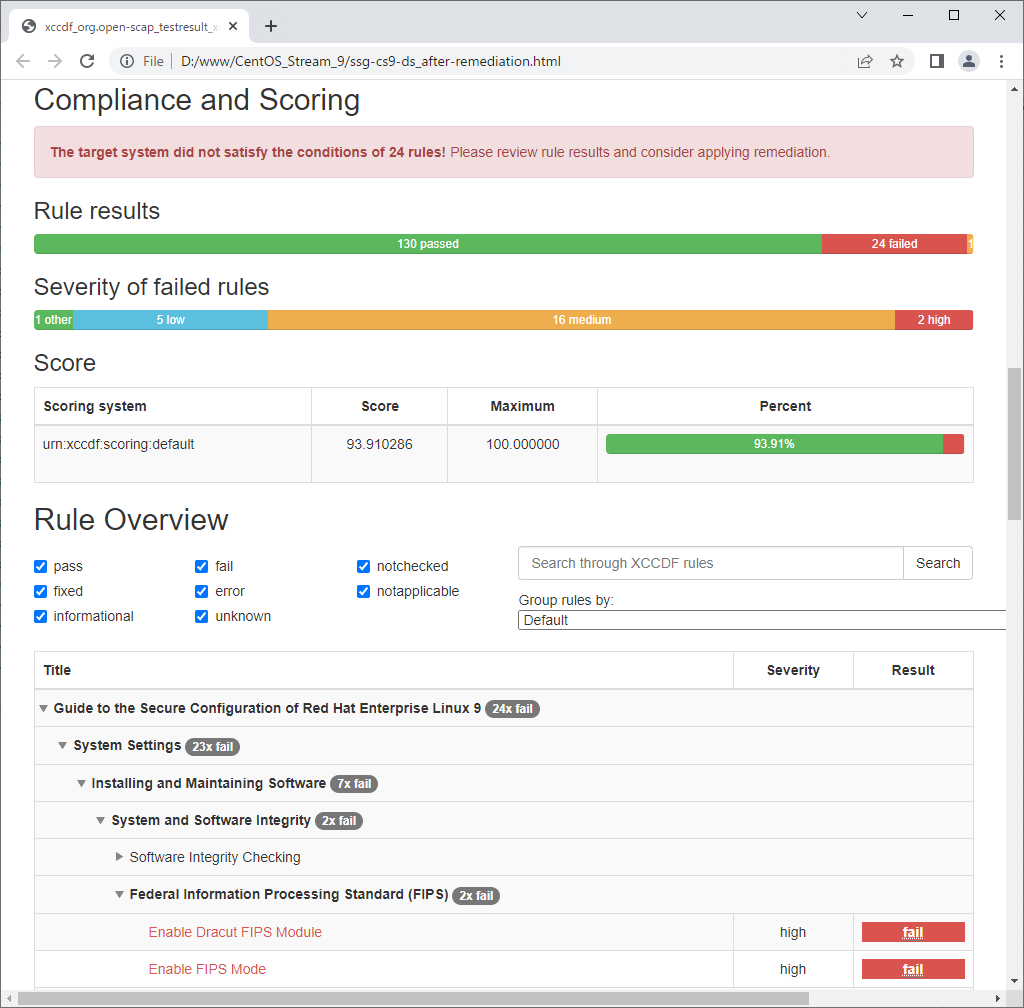
--fix-type bash \ --output ssg-cs9-ds-remediation.sh \ --result-id xccdf_org.open-scap_testresult_xccdf_org.ssgproject.content_profile_ospp \ ssg-cs9-ds.xml total 16172 -rw-------. 1 root root 1100 Nov 26 2021 anaconda-ks.cfg -rw-r--r--. 1 root root 2286030 Jul 29 09:37 ssg-cs9-ds.html -rwx------. 1 root root 183754 Jul 29 09:55 ssg-cs9-ds-remediation.sh -rw-r--r--. 1 root root 14081044 Jul 29 09:37 ssg-cs9-ds.xml # run remediation script [root@dlp ~]# ./ssg-cs9-ds-remediation.sh ..... ..... Remediating rule 111/112: 'xccdf_org.ssgproject.content_rule_service_usbguard_enabled' Created symlink /etc/systemd/system/basic.target.wants/usbguard.service ü© /usr/lib/systemd/system/usbguard.service. Remediating rule 112/112: 'xccdf_org.ssgproject.content_rule_usbguard_allow_hid_and_hub' # check again [root@dlp ~]# oscap xccdf eval \ --profile xccdf_org.ssgproject.content_profile_ospp \ --results ssg-cs9-ds_after-remediation.xml \ --report ssg-cs9-ds_after-remediation.html \ /usr/share/xml/scap/ssg/content/ssg-cs9-ds.xml |
| After running remediation script, many [fail] items has been improved. |
|
Matched Content