HAProxy : ACL Settings2022/03/22 |
|
It's possible to distribute requests to backend servers according to rules to set HAProxy ACL.
This example is based on the environment like follows.
It needs you set DNS to receive requests of hostnames or domainnames you set ACL on HAProxy server.
-----------+-------------+
| |
|10.0.0.30 |
+----------+-----------+ |
| [ dlp.srv.world ] | |
| HAProxy | |
+----------------------+ |
|
-------------+-----------+--------------+----------
| | |
|10.0.0.51 | |10.0.0.52
+-----------+----------+ | +-----------+----------+
| [ node01.srv.world ] | | | [ node02.srv.world ] |
| Web Server#1 | | | Web Server#2 |
+----------------------+ | +----------------------+
|
-------------+-----------+--------------+----------
| |
|10.0.0.53 |10.0.0.31
+-----------+----------+ +-----------+----------+
| [ node03.srv.world ] | | [ www.srv.world ] |
| Web Server#3 | | Web Server#4 |
+----------------------+ +----------------------+
|
| [1] |
The syntax of ACL is like follows.
acl <aclname> <criterion> [flags] [operator] [<value>] ...
For <aclname>, specify any ACL name you like, for [operator], some criteria support an operator.
For others, see official documents below.
⇒ https://www.haproxy.com/documentation/hapee/latest/onepage/#7.3.6
Follows are the list of criteria and flags that are expected to be often used.
|
| [2] | Configure HAProxy. |
|
[root@dlp ~]#
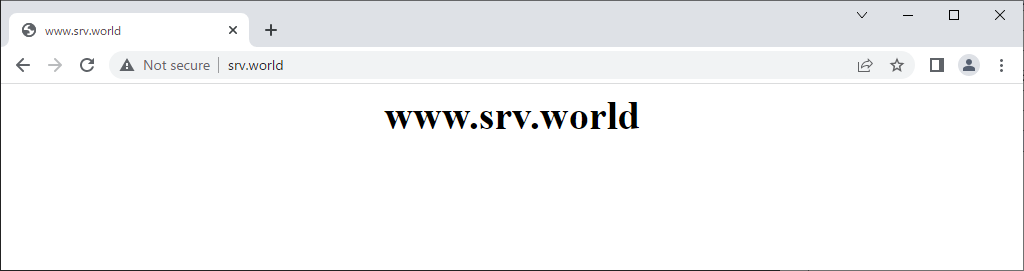
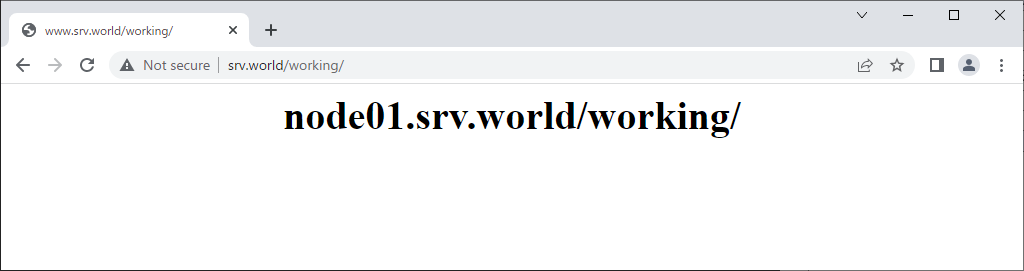
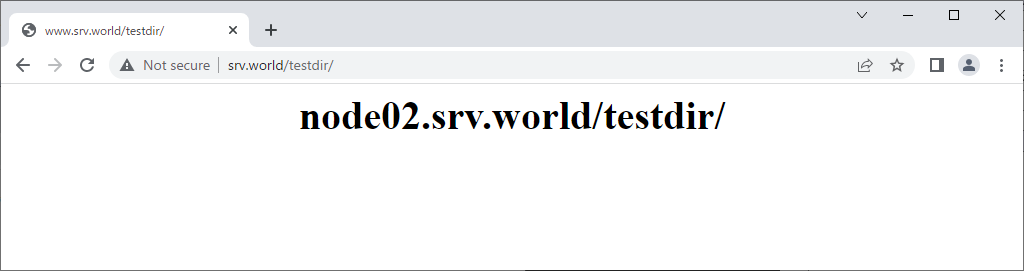
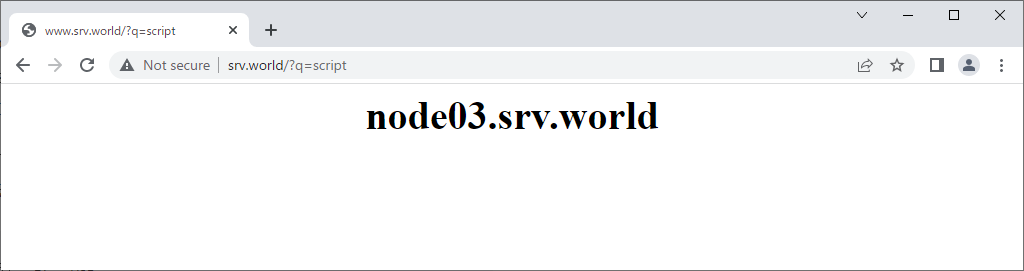
vi /etc/haproxy/haproxy.cfg # add to the end frontend http-in bind *:80 option forwardfor # set ACL # [Host] in HTTP request header is [node01.srv.world] acl host_node01 hdr(Host) -i node01.srv.world # [Host] in HTTP request header begins with [node02] acl host_node02 hdr_beg(Host) -i node02 # [Host] in HTTP request header contains [develop] acl host_node03 hdr_sub(Host) -i develop # domain name of [Host] in HTTP request header is [virtual.host] acl host_virtual_host hdr_dom(Host) -i virtual.host # PATH in HTTP request begins with [/work] acl path_workdir path -m beg /work # PATH in HTTP request contains [test] acl path_testdir path_sub -i test # query in HTTP request contains [script] acl query_script query -m sub script # source client IP address is [10.0.0.5/32] acl src_ip src -m ip 10.0.0.5/32 # set action for each ACL use_backend www_node01 if host_node01 || path_workdir use_backend www_node02 if host_node02 || path_testdir use_backend www_node03 if host_node03 || query_script use_backend www_default if host_virtual_host || src_ip default_backend www_default backend www_node01 server node01 10.0.0.51:80 check backend www_node02 server node02 10.0.0.52:80 check backend www_node03 server node03 10.0.0.53:80 check backend www_default server www_default 10.0.0.31:80 check systemctl restart haproxy |
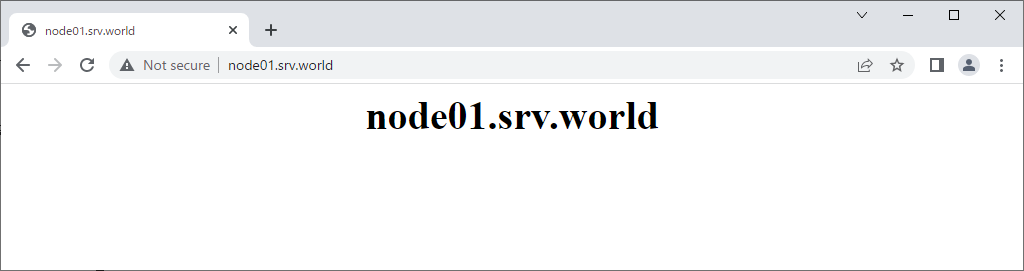
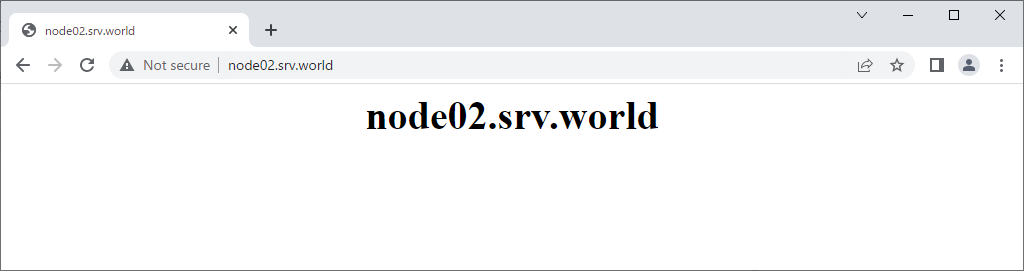
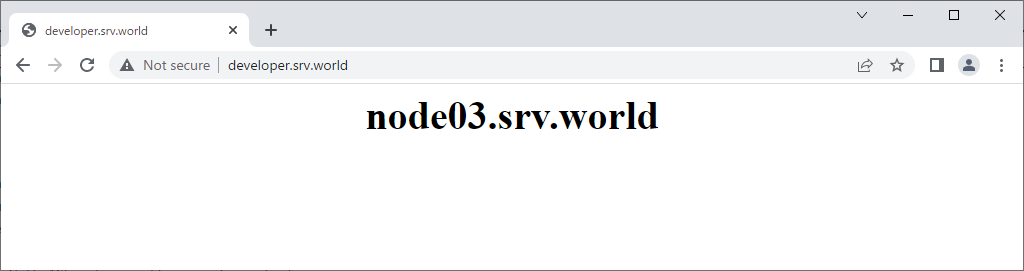
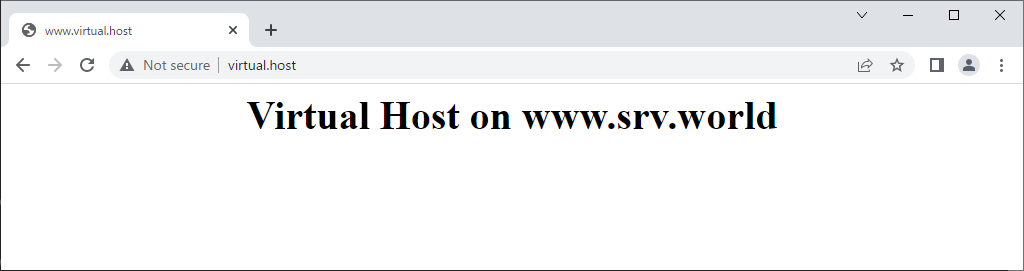
| [3] | Verify working normally to access to the frontend HAproxy Server with each matching pattern. |
|
|
|
|
|
|
|
|
Matched Content