OpenSCAP : Install2022/07/01 |
|
Install OpenSCAP which is the security audit and vulnerability scanning tool based on SCAP (Security Content Automation Protocol).
For details about SCAP, refer to the site below.
⇒ https://csrc.nist.gov/projects/security-content-automation-protocol OVAL (Open Vulnerability and Assessment Language) XCCDF (Extensible Configuration Checklist Description Format) OCIL (Open Checklist Interactive Language) CPE (Common Platform Enumeration) CCE (Common Configuration Enumeration) CVE (Common Vulnerabilities and Exposures) CVSS (Common Vulnerability Scoring System) |
|
| [1] | Install OpenSCAP command line tool and SCAP Security Guide for Linux. |
|
[root@dlp ~]# dnf -y install openscap-scanner scap-security-guide
|
| [2] | SCAP Security Guide is installed under the [/usr/share/xml/scap/ssg/content] directory. |
|
[root@dlp ~]# ll /usr/share/xml/scap/ssg/content/ total 300008 -rw-r--r--. 1 root root 20969763 Jun 9 18:10 ssg-centos7-ds-1.2.xml -rw-r--r--. 1 root root 20970105 Jun 9 18:10 ssg-centos7-ds.xml -rw-r--r--. 1 root root 13787923 Jun 9 18:09 ssg-centos7-xccdf.xml -rw-r--r--. 1 root root 22289156 Jun 9 18:10 ssg-centos8-ds-1.2.xml -rw-r--r--. 1 root root 22289498 Jun 9 18:10 ssg-centos8-ds.xml -rw-r--r--. 1 root root 14480558 Jun 9 18:10 ssg-centos8-xccdf.xml -rw-r--r--. 1 root root 591 Jun 9 18:08 ssg-firefox-cpe-dictionary.xml -rw-r--r--. 1 root root 3885 Jun 9 18:08 ssg-firefox-cpe-oval.xml -rw-r--r--. 1 root root 277332 Jun 9 18:08 ssg-firefox-ds-1.2.xml -rw-r--r--. 1 root root 277332 Jun 9 18:08 ssg-firefox-ds.xml -rw-r--r--. 1 root root 47457 Jun 9 18:08 ssg-firefox-ocil.xml -rw-r--r--. 1 root root 65954 Jun 9 18:08 ssg-firefox-oval.xml -rw-r--r--. 1 root root 144854 Jun 9 18:08 ssg-firefox-xccdf.xml -rw-r--r--. 1 root root 1231 Jun 9 18:08 ssg-jre-cpe-dictionary.xml -rw-r--r--. 1 root root 6349 Jun 9 18:08 ssg-jre-cpe-oval.xml -rw-r--r--. 1 root root 219353 Jun 9 18:08 ssg-jre-ds-1.2.xml -rw-r--r--. 1 root root 219353 Jun 9 18:08 ssg-jre-ds.xml -rw-r--r--. 1 root root 34672 Jun 9 18:08 ssg-jre-ocil.xml -rw-r--r--. 1 root root 44155 Jun 9 18:08 ssg-jre-oval.xml -rw-r--r--. 1 root root 121469 Jun 9 18:08 ssg-jre-xccdf.xml -rw-r--r--. 1 root root 6768 Jun 9 18:10 ssg-rhel6-cpe-dictionary.xml -rw-r--r--. 1 root root 93922 Jun 9 18:10 ssg-rhel6-cpe-oval.xml -rw-r--r--. 1 root root 22934702 Jun 9 18:10 ssg-rhel6-ds-1.2.xml -rw-r--r--. 1 root root 22935173 Jun 9 18:10 ssg-rhel6-ds.xml -rw-r--r--. 1 root root 733916 Jun 9 18:10 ssg-rhel6-ocil.xml -rw-r--r--. 1 root root 2335663 Jun 9 18:10 ssg-rhel6-oval.xml -rw-r--r--. 1 root root 7439626 Jun 9 18:10 ssg-rhel6-xccdf.xml -rw-r--r--. 1 root root 10135 Jun 9 18:09 ssg-rhel7-cpe-dictionary.xml -rw-r--r--. 1 root root 124400 Jun 9 18:09 ssg-rhel7-cpe-oval.xml -rw-r--r--. 1 root root 22186207 Jun 9 18:09 ssg-rhel7-ds-1.2.xml -rw-r--r--. 1 root root 22186549 Jun 9 18:09 ssg-rhel7-ds.xml -rw-r--r--. 1 root root 1629296 Jun 9 18:09 ssg-rhel7-ocil.xml -rw-r--r--. 1 root root 4763301 Jun 9 18:09 ssg-rhel7-oval.xml -rw-r--r--. 1 root root 14595795 Jun 9 18:09 ssg-rhel7-xccdf.xml -rw-r--r--. 1 root root 13099 Jun 9 18:09 ssg-rhel8-cpe-dictionary.xml -rw-r--r--. 1 root root 124400 Jun 9 18:09 ssg-rhel8-cpe-oval.xml -rw-r--r--. 1 root root 23307942 Jun 9 18:10 ssg-rhel8-ds-1.2.xml -rw-r--r--. 1 root root 23308284 Jun 9 18:10 ssg-rhel8-ds.xml -rw-r--r--. 1 root root 1785009 Jun 9 18:09 ssg-rhel8-ocil.xml -rw-r--r--. 1 root root 5204724 Jun 9 18:09 ssg-rhel8-oval.xml -rw-r--r--. 1 root root 15155753 Jun 9 18:09 ssg-rhel8-xccdf.xml # display description for each content [root@dlp ~]# oscap info /usr/share/xml/scap/ssg/content/ssg-centos8-ds-1.2.xml
Document type: Source Data Streamre/xml/scap/ssg/content/ssg-centos8-ds-1.2.xml
Imported: 2022-06-09T18:10:12
Stream: scap_org.open-scap_datastream_from_xccdf_ssg-rhel8-xccdf-1.2.xml
Generated: (null)
Version: 1.2
Checklists:
Ref-Id: scap_org.open-scap_cref_ssg-rhel8-xccdf-1.2.xml
Status: draft
Generated: 2022-06-09
Resolved: true
Profiles:
Title: PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 8
Id: xccdf_org.ssgproject.content_profile_pci-dss
Referenced check files:
ssg-rhel8-oval.xml
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
ssg-rhel8-ocil.xml
system: http://scap.nist.gov/schema/ocil/2
https://access.redhat.com/security/data/oval/com.redhat.rhsa-RHEL8.xml.bz2
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
Checks:
Ref-Id: scap_org.open-scap_cref_ssg-rhel8-oval.xml
Ref-Id: scap_org.open-scap_cref_ssg-rhel8-ocil.xml
Ref-Id: scap_org.open-scap_cref_ssg-rhel8-cpe-oval.xml
Dictionaries:
Ref-Id: scap_org.open-scap_cref_ssg-rhel8-cpe-dictionary.xml
|
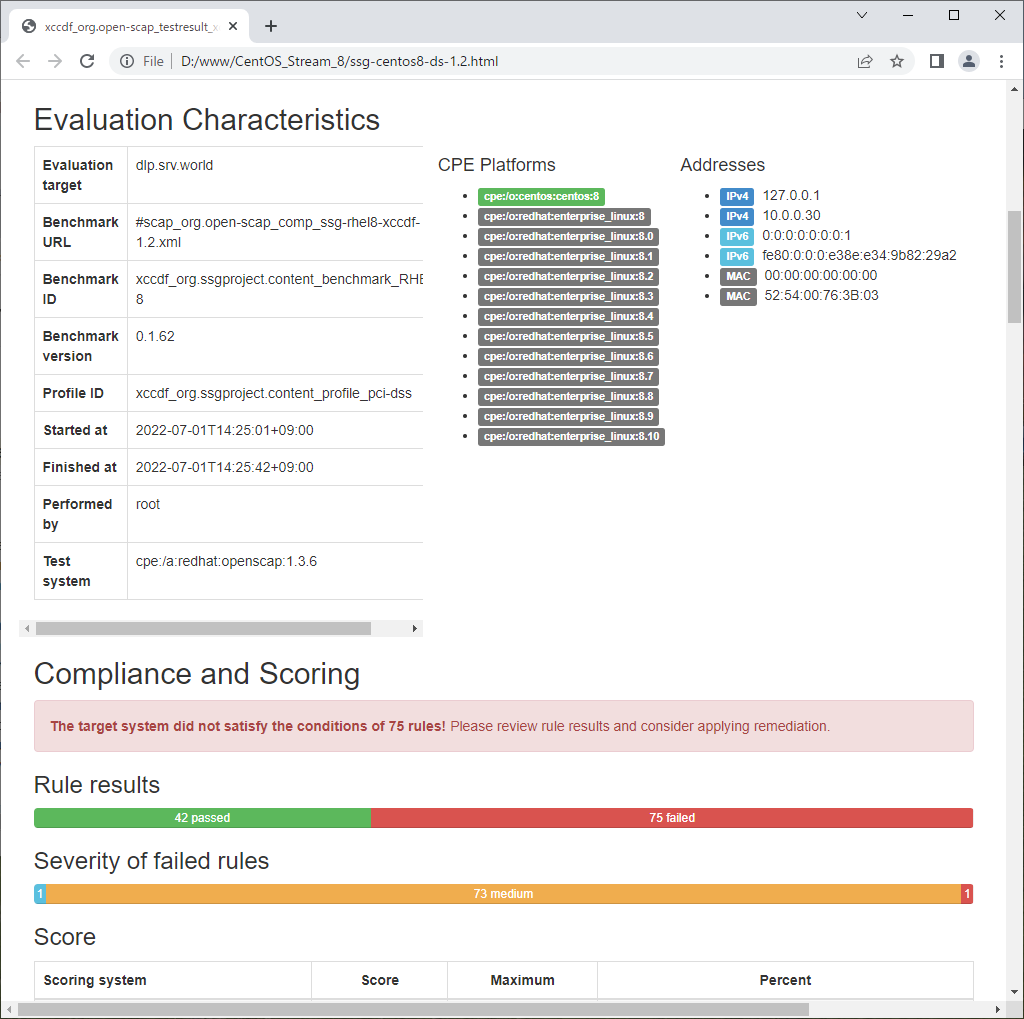
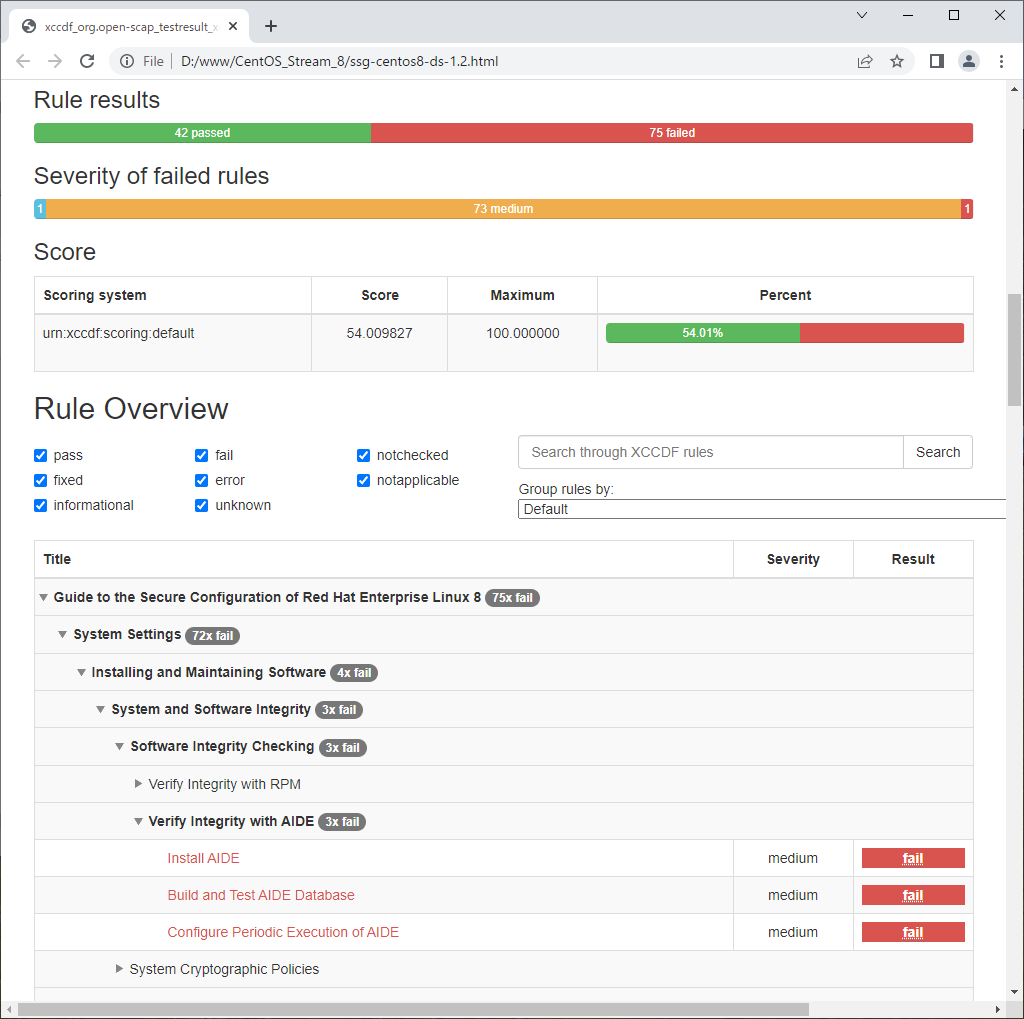
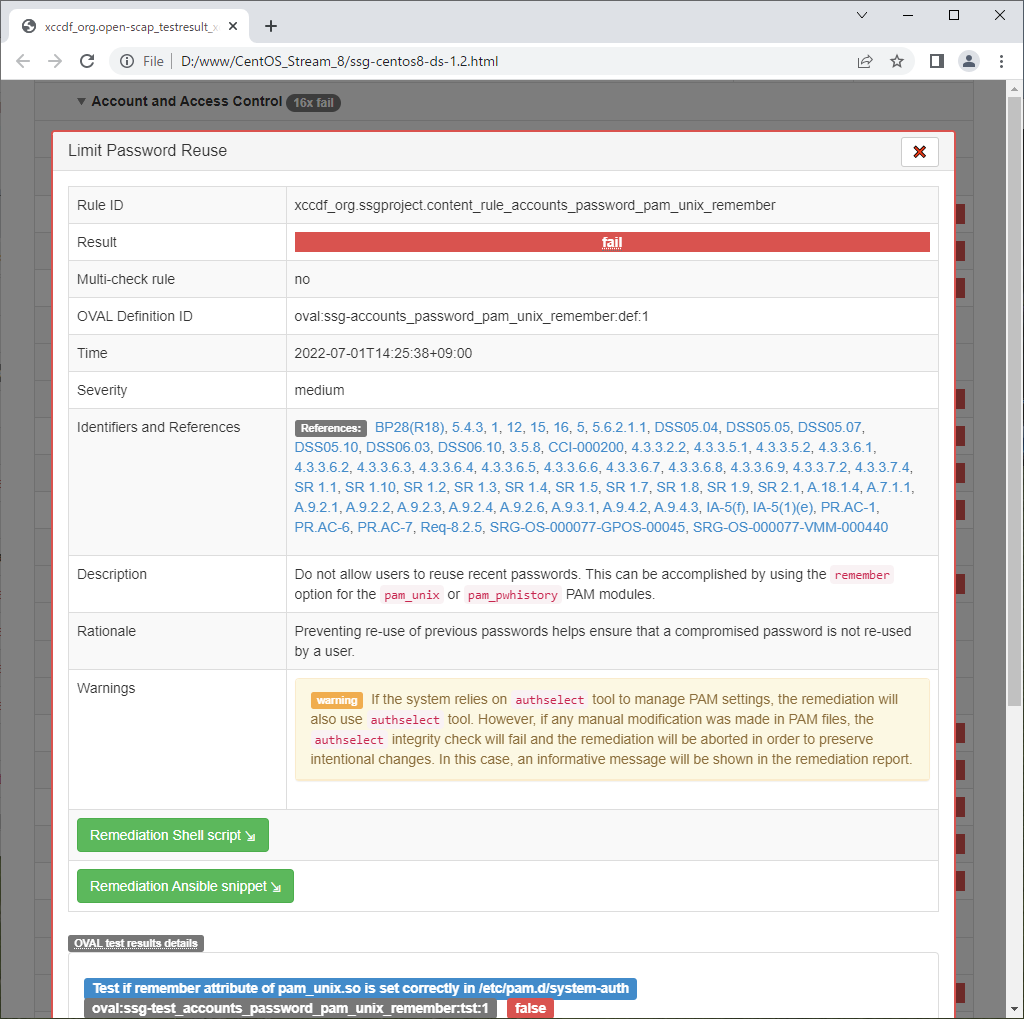
| [3] | Scan CentOS System with [oscap] command. Scan result is renerated as HTML report, you should verify it and try to apply recommended settings as much as possible. |
|
# xccdf : specify [xccdf] module
# ⇒ available modules : info, xccdf, oval, ds, cpe, cvss, cve, cvrf # [--profile] : specify profile # ⇒ available profiles are on the result you run [oscap info] command above # [--results] : output file # [--report] : output HTML report # [--fetch-remote-resources] : download the latest data oscap xccdf eval \ --profile xccdf_org.ssgproject.content_profile_pci-dss \ --results ssg-centos8-ds-1.2.xml \ --report ssg-centos8-ds-1.2.html \ --fetch-remote-resources \ /usr/share/xml/scap/ssg/content/ssg-centos8-ds-1.2.xml Downloading: https://access.redhat.com/security/data/oval/com.redhat.rhsa-RHEL8.xml.bz2 ... ok --- Starting Evaluation --- Title Verify File Hashes with RPM Rule xccdf_org.ssgproject.content_rule_rpm_verify_hashes Result pass Title Verify and Correct File Permissions with RPM Rule xccdf_org.ssgproject.content_rule_rpm_verify_permissions Result pass Title Install AIDE Rule xccdf_org.ssgproject.content_rule_package_aide_installed Result fail Title Build and Test AIDE Database Rule xccdf_org.ssgproject.content_rule_aide_build_database Result fail Title Configure Periodic Execution of AIDE Rule xccdf_org.ssgproject.content_rule_aide_periodic_cron_checking Result fail Title Configure BIND to use System Crypto Policy Rule xccdf_org.ssgproject.content_rule_configure_bind_crypto_policy Result pass Title Configure System Cryptography Policy Rule xccdf_org.ssgproject.content_rule_configure_crypto_policy Result pass Title Configure Kerberos to use System Crypto Policy Rule xccdf_org.ssgproject.content_rule_configure_kerberos_crypto_policy Result pass Title Configure Libreswan to use System Crypto Policy Rule xccdf_org.ssgproject.content_rule_configure_libreswan_crypto_policy Result pass Title Configure OpenSSL library to use System Crypto Policy Rule xccdf_org.ssgproject.content_rule_configure_openssl_crypto_policy Result pass Title Configure SSH to use System Crypto Policy Rule xccdf_org.ssgproject.content_rule_configure_ssh_crypto_policy Result pass Title Install Intrusion Detection Software Rule xccdf_org.ssgproject.content_rule_install_hids Result pass Title Make sure that the dconf databases are up-to-date with regards to respective keyfiles Rule xccdf_org.ssgproject.content_rule_dconf_db_up_to_date Result notapplicable ..... ..... |
|
|
|
|
| [4] |
It's possible to generate remediation script from scaned result.
Remediation script will change various system settings, so you must take care if you run it, especially for production systems.
|
|
# make sure the [Result ID] in the result output on [3] [root@dlp ~]# oscap info ssg-centos8-ds-1.2.xml | grep "Result ID"
Result ID: xccdf_org.open-scap_testresult_xccdf_org.ssgproject.content_profile_pci-dss
# generate remediation script
# [--fix-type] : specify fix type : default is Bash # ⇒ available type : bash, ansible, puppet, anaconda, ignition, kubernetes, blueprint # [--output] : specify output script file # [--result-id] : specify [Result ID]
[root@dlp ~]#
[root@dlp ~]# oscap xccdf generate fix \
--fix-type bash \ --output ssg-centos8-ds-1.2-remediation.sh \ --result-id xccdf_org.open-scap_testresult_xccdf_org.ssgproject.content_profile_pci-dss \ ssg-centos8-ds-1.2.xml total 19160 -rw-------. 1 root root 1349 Feb 18 2021 anaconda-ks.cfg -rw-r--r--. 1 root root 4093426 Jul 29 11:03 ssg-centos8-ds-1.2.html -rwx------. 1 root root 805485 Jul 29 11:04 ssg-centos8-ds-1.2-remediation.sh -rw-r--r--. 1 root root 14709313 Jul 29 11:02 ssg-centos8-ds-1.2.xml # run remediation script [root@dlp ~]# ./ssg-centos8-ds-1.2-remediation.sh ..... ..... Remediating rule 75/77: 'xccdf_org.ssgproject.content_rule_chronyd_or_ntpd_specify_multiple_servers' Remediating rule 76/77: 'xccdf_org.ssgproject.content_rule_sshd_set_keepalive_0' Remediating rule 77/77: 'xccdf_org.ssgproject.content_rule_sshd_set_idle_timeout' # check again [root@dlp ~]# oscap xccdf eval \ --profile xccdf_org.ssgproject.content_profile_pci-dss \ --results ssg-centos8-ds-1.2_after-remediation.xml \ --report ssg-centos8-ds-1.2_after-remediation.html \ --fetch-remote-resources \ /usr/share/xml/scap/ssg/content/ssg-centos8-ds-1.2.xml |
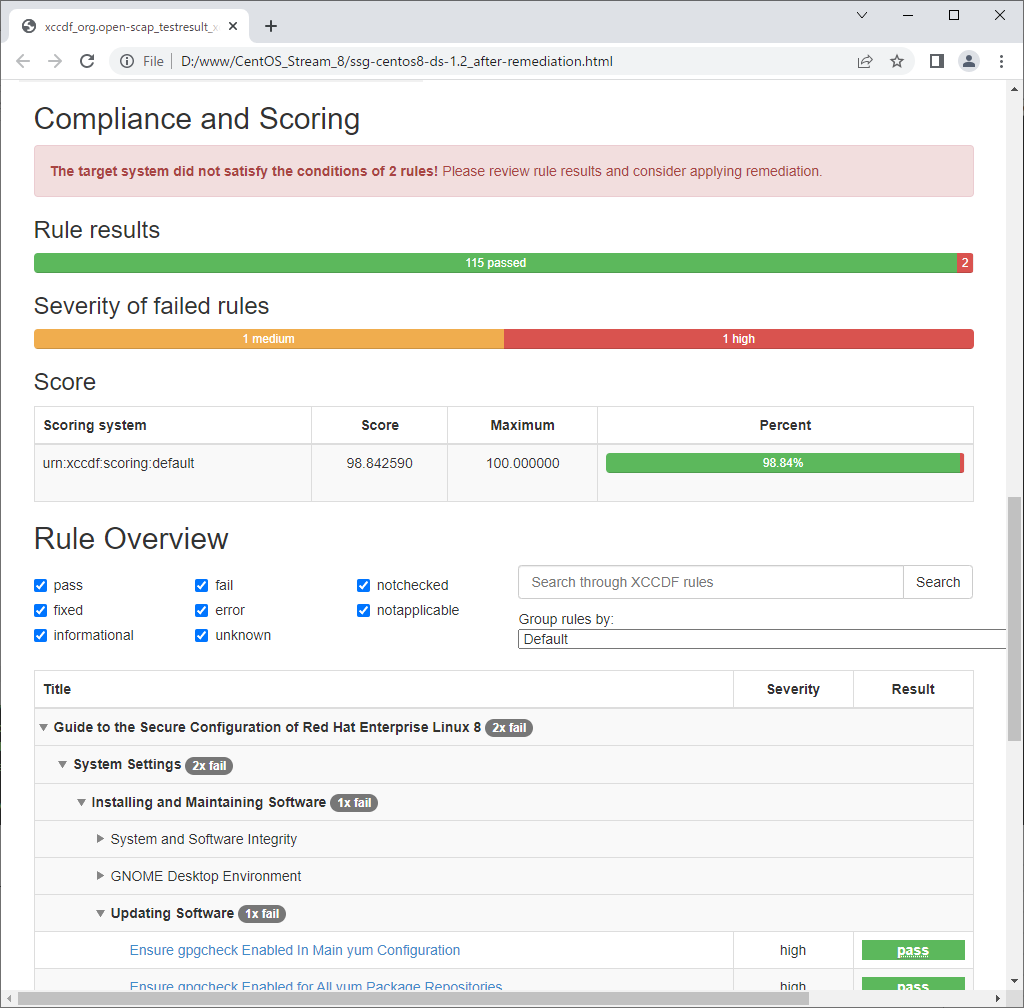
| After running remediation script, many [fail] items has been improved. |
|
Matched Content