Apache httpd : Configure mod_security2021/03/15 |
|
Enable [mod_security] module to configure Web Application Firewall (WAF).
|
|
| [1] | Install [mod_security]. |
|
[root@www ~]# dnf -y install mod_security
|
| [2] | After installing, configuration files are placed under the directory like follows and the setting is enabled. Some settings are already set in it and also you can add your own rules. |
|
[root@www ~]# cat /etc/httpd/conf.d/mod_security.conf
<IfModule mod_security2.c>
# Default recommended configuration
SecRuleEngine On
SecRequestBodyAccess On
SecRule REQUEST_HEADERS:Content-Type "text/xml" \
"id:'200000',phase:1,t:none,t:lowercase,pass,nolog,ctl:requestBodyProcessor=XML"
SecRequestBodyLimit 13107200
SecRequestBodyNoFilesLimit 131072
SecRequestBodyInMemoryLimit 131072
SecRequestBodyLimitAction Reject
SecRule REQBODY_ERROR "!@eq 0" \
.....
.....
# if you would not like to block requests if matchs rules,
# specify change to the parameter [SecRuleEngine DetectionOnly] |
| [3] |
It's possible to write a rule like follows.
⇒ SecRule VARIABLES OPERATOR [ACTIONS]
Each parameter has many kind of values, refer to official documents below.
https://github.com/SpiderLabs/ModSecurity/wiki |
| [4] | For Exmaple, set some rules and verify it works normally. |
|
[root@www ~]#
vi /etc/httpd/modsecurity.d/local_rules/modsecurity_localrules.conf # default action when matching rules SecDefaultAction "phase:2,deny,log,status:406" # [etc/passwd] is included in request URI SecRule REQUEST_URI "etc/passwd" "id:'500001'" # [../] is included in request URI SecRule REQUEST_URI "\.\./" "id:'500002'" # [<SCRIPT] is included in arguments SecRule ARGS "<[Ss][Cc][Rr][Ii][Pp][Tt]" "id:'500003'" # [SELECT FROM] is included in arguments SecRule ARGS "[Ss][Ee][Ll][Ee][Cc][Tt][[:space:]]+[Ff][Rr][Oo][Mm]" "id:'500004'" systemctl restart httpd
|
| [5] | Access to the URI which includes words you set and verify it works normally. |
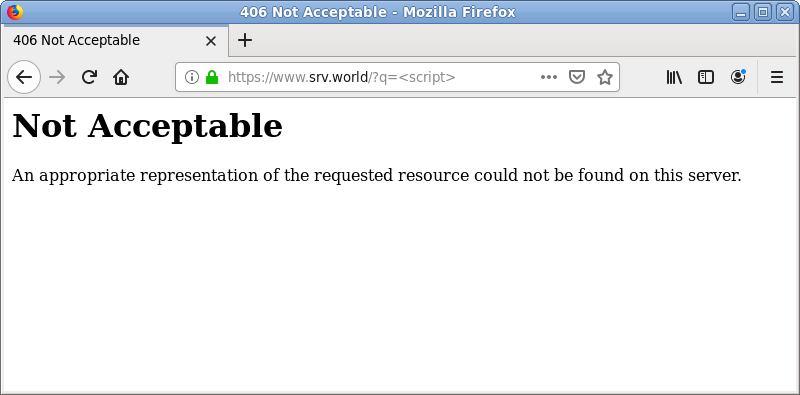
|
| [6] | The logs for [mod_security] is placed in the directory like follows. |
|
[root@www ~]# cat /var/log/httpd/modsec_audit.log --d485da28-A-- [12/Mar/2021:00:06:39 --0600] YEsE73MybhCt0szpdYY7uAAAAFU 10.0.0.18 43530 10.0.0.31 443 --d485da28-B-- GET /?q=%3Cscript%3E HTTP/1.1 Host: www.srv.world User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate, br DNT: 1 Connection: keep-alive Upgrade-Insecure-Requests: 1 --d485da28-F-- HTTP/1.1 406 Not Acceptable Content-Length: 249 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html; charset=iso-8859-1 --d485da28-E-- --d485da28-H-- Message: Access denied with code 406 (phase 2). Pattern match "<[Ss][Cc][Rr][Ii][Pp][Tt]" at ARGS:q. [file "/etc/httpd/modsecurity.d/local_rules/modsecurity_localrules.conf"] [line "12"] [id "500003"] Apache-Error: [file "apache2_util.c"] [line 273] [level 3] [client 10.0.0.18] ModSecurity: Access denied with code 406 (phase 2). Pattern match "<[Ss][Cc][Rr][Ii][Pp][Tt]" at ARGS:q. [file "/etc/httpd/modsecurity.d/local_rules/modsecurity_localrules.conf"] [line "12"] [id "500003"] [hostname "www.srv.world"] [uri "/"] [unique_id "YEsE73MybhCt0szpdYY7uAAAAFU"] Action: Intercepted (phase 2) Stopwatch: 1615529199689509 1309 (- - -) Stopwatch2: 1615529199689509 1309; combined=79, p1=10, p2=66, p3=0, p4=0, p5=3, sr=0, sw=0, l=0, gc=0 Response-Body-Transformed: Dechunked Producer: ModSecurity for Apache/2.9.2 (http://www.modsecurity.org/). Server: Apache Engine-Mode: "ENABLED" ..... ..... |
| [7] | General rules are provided from official repository and it's easy to apply them like follows. But maybe you need to customize them for your own web sites not to block necessary requests. |
|
[root@www ~]#
dnf -y install mod_security_crs # rules are placed like follows # they are linked into the directory [/etc/httpd/modsecurity.d/activated_rules] [root@www ~]# ll /usr/share/mod_modsecurity_crs/rules total 544 -rw-r--r--. 1 root root 659 May 13 2019 crawlers-user-agents.data -rw-r--r--. 1 root root 551 May 13 2019 iis-errors.data -rw-r--r--. 1 root root 264 May 13 2019 java-code-leakages.data -rw-r--r--. 1 root root 240 May 13 2019 java-errors.data -rw-r--r--. 1 root root 30167 May 13 2019 lfi-os-files.data -rw-r--r--. 1 root root 5409 May 13 2019 php-config-directives.data -rw-r--r--. 1 root root 9144 May 13 2019 php-errors.data -rw-r--r--. 1 root root 589 May 13 2019 php-function-names-933150.data -rw-r--r--. 1 root root 21376 May 13 2019 php-function-names-933151.data -rw-r--r--. 1 root root 224 May 13 2019 php-variables.data -rw-r--r--. 1 root root 10363 May 13 2019 REQUEST-901-INITIALIZATION.conf -rw-r--r--. 1 root root 13332 May 13 2019 REQUEST-903.9001-DRUPAL-EXCLUSION-RULES.conf -rw-r--r--. 1 root root 15476 May 13 2019 REQUEST-903.9002-WORDPRESS-EXCLUSION-RULES.conf -rw-r--r--. 1 root root 1394 May 13 2019 REQUEST-905-COMMON-EXCEPTIONS.conf -rw-r--r--. 1 root root 10155 May 13 2019 REQUEST-910-IP-REPUTATION.conf -rw-r--r--. 1 root root 2679 May 13 2019 REQUEST-911-METHOD-ENFORCEMENT.conf -rw-r--r--. 1 root root 8582 May 13 2019 REQUEST-912-DOS-PROTECTION.conf -rw-r--r--. 1 root root 7590 May 13 2019 REQUEST-913-SCANNER-DETECTION.conf -rw-r--r--. 1 root root 47012 May 13 2019 REQUEST-920-PROTOCOL-ENFORCEMENT.conf -rw-r--r--. 1 root root 12577 May 13 2019 REQUEST-921-PROTOCOL-ATTACK.conf -rw-r--r--. 1 root root 6362 May 13 2019 REQUEST-930-APPLICATION-ATTACK-LFI.conf -rw-r--r--. 1 root root 5735 May 13 2019 REQUEST-931-APPLICATION-ATTACK-RFI.conf -rw-r--r--. 1 root root 47293 May 13 2019 REQUEST-932-APPLICATION-ATTACK-RCE.conf -rw-r--r--. 1 root root 30948 May 13 2019 REQUEST-933-APPLICATION-ATTACK-PHP.conf -rw-r--r--. 1 root root 40051 May 13 2019 REQUEST-941-APPLICATION-ATTACK-XSS.conf -rw-r--r--. 1 root root 57035 May 13 2019 REQUEST-942-APPLICATION-ATTACK-SQLI.conf -rw-r--r--. 1 root root 5459 May 13 2019 REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.conf -rw-r--r--. 1 root root 3190 May 13 2019 REQUEST-949-BLOCKING-EVALUATION.conf -rw-r--r--. 1 root root 3812 May 13 2019 RESPONSE-950-DATA-LEAKAGES.conf -rw-r--r--. 1 root root 19941 May 13 2019 RESPONSE-951-DATA-LEAKAGES-SQL.conf -rw-r--r--. 1 root root 3792 May 13 2019 RESPONSE-952-DATA-LEAKAGES-JAVA.conf -rw-r--r--. 1 root root 5154 May 13 2019 RESPONSE-953-DATA-LEAKAGES-PHP.conf -rw-r--r--. 1 root root 5994 May 13 2019 RESPONSE-954-DATA-LEAKAGES-IIS.conf -rw-r--r--. 1 root root 2843 May 13 2019 RESPONSE-959-BLOCKING-EVALUATION.conf -rw-r--r--. 1 root root 4410 May 13 2019 RESPONSE-980-CORRELATION.conf -rw-r--r--. 1 root root 713 May 13 2019 restricted-files.data -rw-r--r--. 1 root root 216 May 13 2019 scanners-headers.data -rw-r--r--. 1 root root 418 May 13 2019 scanners-urls.data -rw-r--r--. 1 root root 4075 May 13 2019 scanners-user-agents.data -rw-r--r--. 1 root root 717 May 13 2019 scripting-user-agents.data -rw-r--r--. 1 root root 1894 May 13 2019 sql-errors.data -rw-r--r--. 1 root root 1981 May 13 2019 sql-function-names.data -rw-r--r--. 1 root root 943 May 13 2019 unix-shell.data -rw-r--r--. 1 root root 3920 May 13 2019 windows-powershell-commands.data |
Matched Content