MicroK8s : Enable Dashboard2020/08/12 |
|
To enable Dashboard on MicroK8s Cluster, Configure like follows.
|
| [1] | Enable Dashboard add-on on primary Node. |
|
[root@dlp ~]# microk8s enable dashboard dns Enabling Kubernetes Dashboard Addon metrics-server is already enabled. Applying manifest serviceaccount/kubernetes-dashboard created service/kubernetes-dashboard created secret/kubernetes-dashboard-certs created secret/kubernetes-dashboard-csrf created secret/kubernetes-dashboard-key-holder created configmap/kubernetes-dashboard-settings created role.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created deployment.apps/kubernetes-dashboard created service/dashboard-metrics-scraper created deployment.apps/dashboard-metrics-scraper created If RBAC is not enabled access the dashboard using the default token retrieved with: token=$(microk8s kubectl -n kube-system get secret | grep default-token | cut -d " " -f1) microk8s kubectl -n kube-system describe secret $token In an RBAC enabled setup (microk8s enable RBAC) you need to create a user with restricted permissions as shown in: https://github.com/kubernetes/dashboard/blob/master/docs/user/access-control/creating-sample-user.md Enabling DNS Applying manifest serviceaccount/coredns created configmap/coredns created deployment.apps/coredns created service/kube-dns created clusterrole.rbac.authorization.k8s.io/coredns created clusterrolebinding.rbac.authorization.k8s.io/coredns created Restarting kubelet Adding argument --cluster-domain to nodes. Applying to node node01.srv.world. Node node01.srv.world not present Adding argument --cluster-dns to nodes. Applying to node node01.srv.world. Node node01.srv.world not present Restarting nodes. Applying to node node01.srv.world. Node node01.srv.world not present DNS is enabled[root@dlp ~]# microk8s kubectl get services -n kube-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE dashboard-metrics-scraper ClusterIP 10.152.183.162 <none> 8000/TCP 46s kube-dns ClusterIP 10.152.183.10 <none> 53/UDP,53/TCP,9153/TCP 45s kubernetes-dashboard ClusterIP 10.152.183.65 <none> 443/TCP 46s metrics-server ClusterIP 10.152.183.102 <none> 443/TCP 15h[root@dlp ~]# microk8s kubectl -n kube-system get pods -o wide NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES coredns-588fd544bf-4d4kc 1/1 Running 0 24s 10.1.68.25 dlp.srv.world <none> <none> dashboard-metrics-scraper-59f5574d4-lmgmt 1/1 Running 0 25s 10.1.68.24 dlp.srv.world <none> <none> kubernetes-dashboard-6d97855997-bwg2g 1/1 Running 0 25s 10.1.68.23 dlp.srv.world <none> <none> metrics-server-c65c9d66-kdxh8 1/1 Running 2 16h 10.1.68.19 dlp.srv.world <none> <none> # confirm security token # it is the second column value on [token:] line [root@dlp ~]# microk8s kubectl -n kube-system describe secret $(microk8s kubectl -n kube-system get secret | grep default-token | awk '{print $1}')
Name: default-token-l5fsn
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: default
kubernetes.io/service-account.uid: 63e24aa4-dabf-4ccf-848e-8993470d03c4
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1103 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlR2azl4Xy1WSFo1VEVtNDZaMFB0TzFaZGtJa0xqR.....
# set port-forwarding to enable external access [root@dlp ~]# microk8s kubectl port-forward -n kube-system service/kubernetes-dashboard --address 0.0.0.0 10443:443 Forwarding from 0.0.0.0:10443 -> 8443 # if Firewalld is running, allow ports [root@dlp ~]# firewall-cmd --add-port=10443/tcp --permanent [root@dlp ~]# firewall-cmd --reload |
| [2] | Access to [https://(MicroK8s primary node's Hostname or IP address):10443/] with an web browser on any Client computer in local network. Copy and paste the security token you confirmed on [1] to [Enter token] section and Click [Sing In] button. |
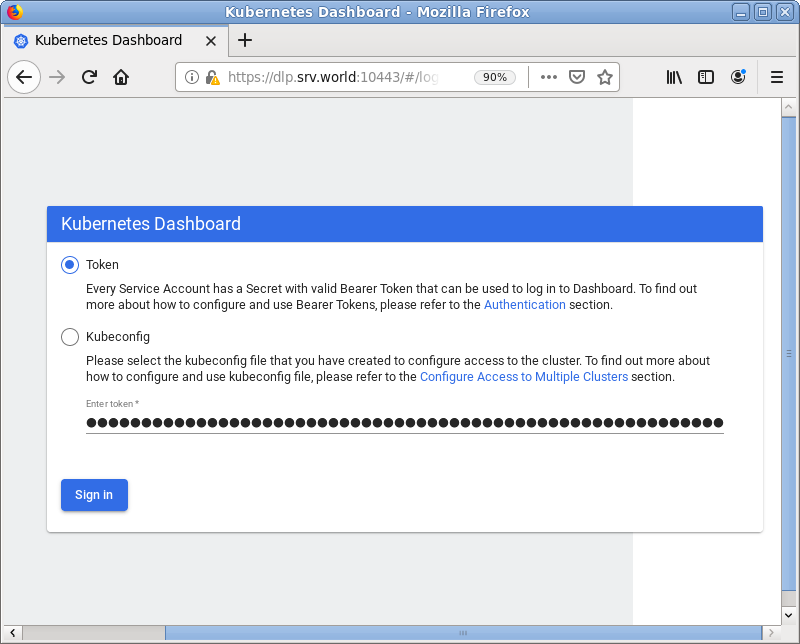
|
| [3] | After authentication successfully passed, MicroK8s Cluster Dashboard is displayed. |
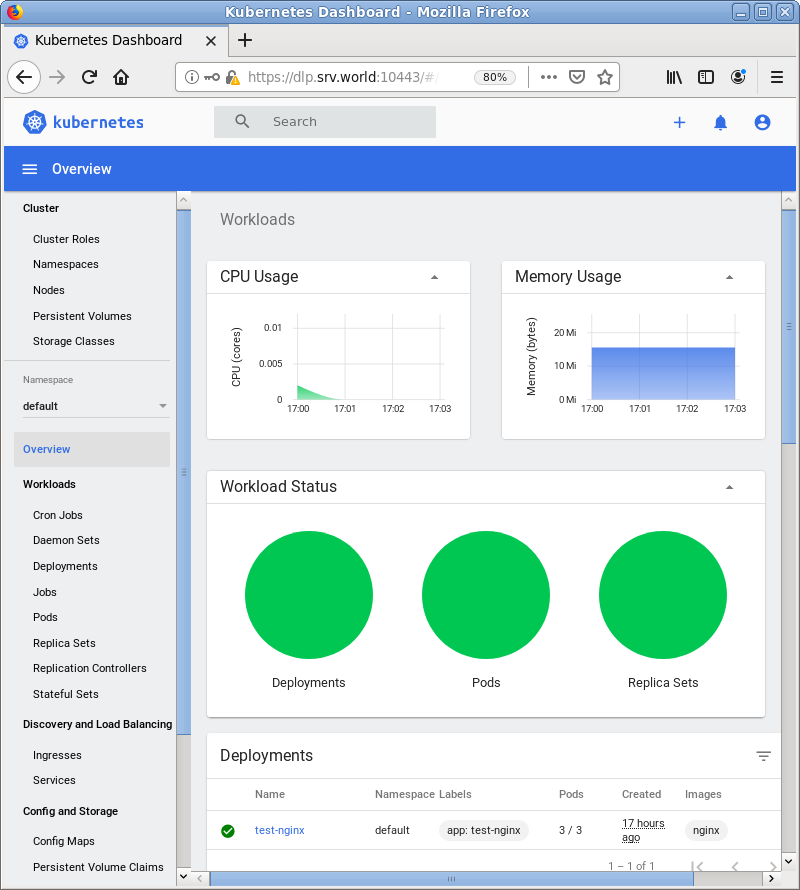
|
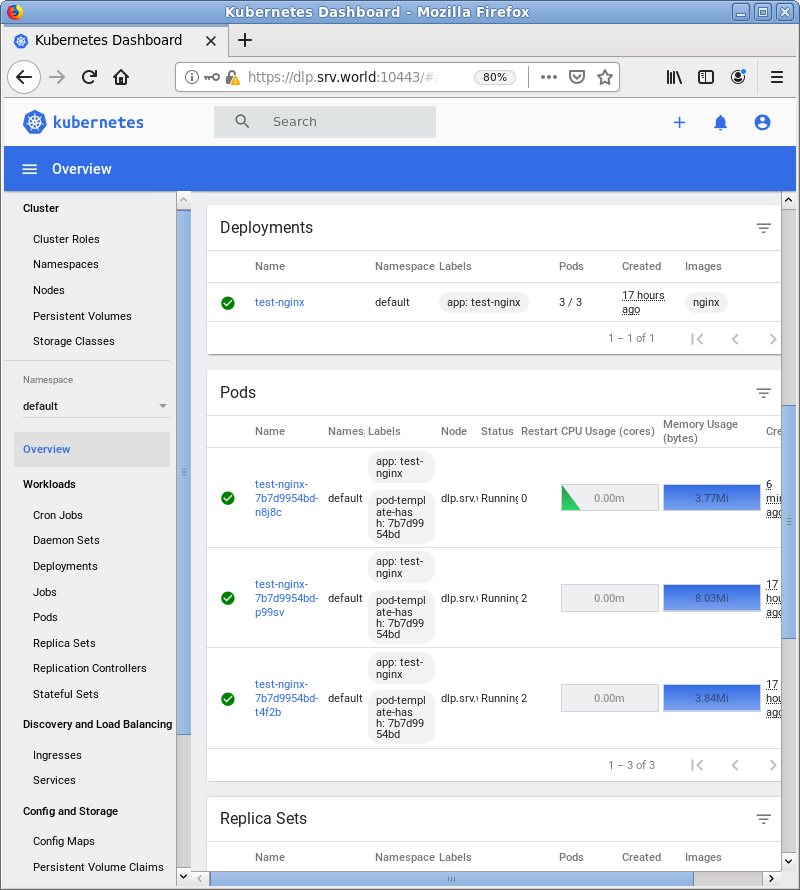
|
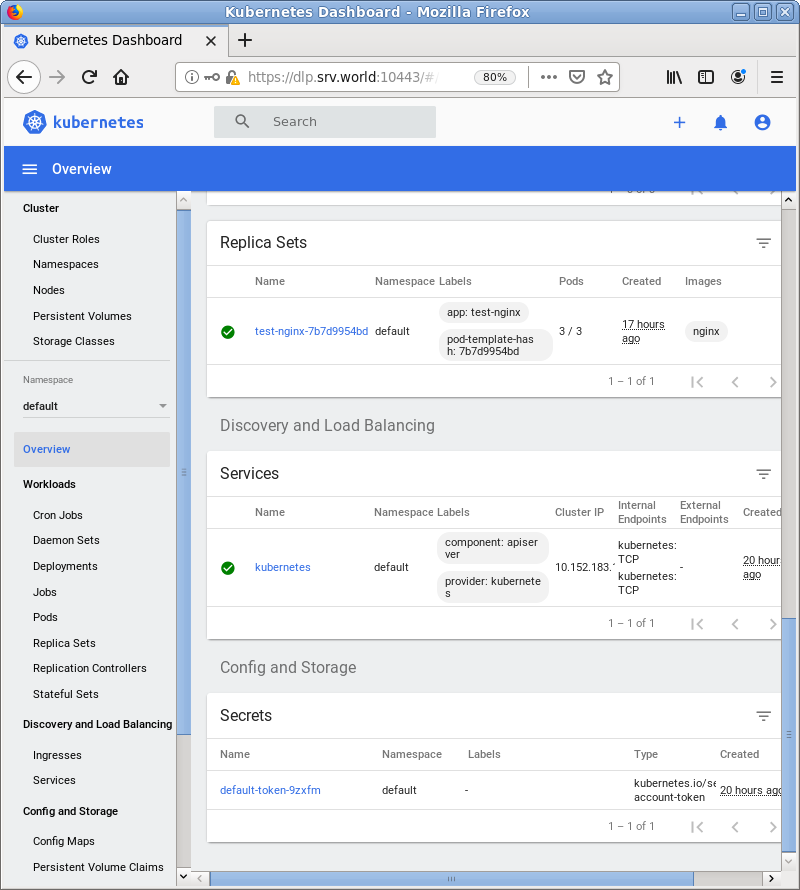
|
Matched Content